Cyberattacks: A New False Flag Frontier
BY KIT KLARENBERG | JULY 15, 2024
At the start of June, Admiral Robert Bauer, head of NATO’s military committee, announced that the military alliance had finalised plans to recognise state-backed cyberattacks on its members as a dedicated pretext for activating Article 5. Reportedly “a joint decision of all allies,” from now on, foreign hacking blitzes can be countered with a collective NATO response, up to and including military measures. Bauer’s disclosure passed the media by entirely – but this is a seismic development, heralding a modern, digital form of ‘false flag’.
Article 5, which provides for collective defence in the event a NATO member is attacked, was a core component of the military alliance’s founding treaty. While it has been invoked just once – by the US, in the wake of 9/11, to invade Afghanistan – there have been efforts to spark it before and since. Most recently, in November 2022, the government of Ukraine falsely declared a missile fired by Kiev that struck Poland, killing two people, was Russian in origin.
The purpose of this deceit was undoubtedly to embroil NATO formally and directly in the proxy war. Wise to the ruse, US officials harshly rebuked President Volodmoyr Zelensky publicly for the World War-threatening fraud. Such incidents amply underline Article 5’s susceptibility to abuse. Yet apparently, military alliance chiefs – and the bloc’s members – are keen to ever-expand its terms, well-beyond its initial remit. Adding cyberattacks to the roster of grounds for collective response is a long-standing objective.
In August 2019, NATO secretary general Jens Stoltenberg authored a bombastic op-ed declaring the military alliance would “guard its cyber domain and invoke collective defence if required.” A “serious cyberattack” on one member state could be “treated as an attack against us all,” he wrote, triggering Article 5 in the process. Fast forward two years, and Keith Alexander, US National Security Agency director 2005 – 2014, called on the ‘Five Eyes’ global spying network to construct a global unified cyberattack “radar”:
“Imagine if we built a radar picture for cyber that covered not only what impacts Australia, but what impacts other countries, and we could share, in real time, threats that are hitting our countries… What we can do is share information and work together… Cyber is going to be hugely important for our future. It’s the one area where adversaries can attack Australia and the US without trying to cross the oceans… We have this anomaly: how are you gonna defend that which you can’t see?”
Alexander, who lied brazenly to the public about his agency’s spying capabilities – including while while testifying under oath to Congress – during his time as NSA chief, suggested this worldwide dragnet would contribute significantly to collective defence, in the obvious spirit of NATO’s Article 5. Given “proposals” for Orwellian, futuristic resources from Western politicians and military and intelligence officials almost invariably presage their real-world rollout, we can only assume in light of Bauer’s announcement such a “radar” is incoming.
‘Security Failures’
This interpretation is reinforced by Bauer observing how invoking Article 5 could only happen once it was confirmed a cyberattack was carried out by a state actor, not a private person or structure. “In that case, it would not be clear who to go to war with,” he added. It’s certainly a source of some relief that NATO is committed to securing clarity on “who to go to war with”, before launching a military “response” to a cyberattack.
However, these comments illuminate a very obvious, grave problem with adding cyberattacks to Article 5’s ambit. Identifying who or what is responsible for them to an absolute certainty is extremely difficult. This task is further complicated by a frequent lack of certainty over whether hackers operating from a particular state are doing so at the behest of authorities. For example, much has been made in Britain recently of Russian hacking group Qilin, which supposedly infiltrated NHS servers.
Mainstream media reports have universally framed Qilin as a malign instrument of the Kremlin, although whether Russian officials command the group, let alone even know of its existence, is far from clear. A representative iNews article refers to Qilin as “a syndicate made up of more than 100 groups…not believed to be under the direct control [emphasis added] of the Russian government.” Instead, Qilin is claimed to be “a useful tool of global disruption the Kremlin is happy to turn a blind eye to.”
Further muddying the picture, it has been confirmed that Western intelligence services can falsely attribute cyberattacks, with devastating effect. In 2017, CIA files published by WikiLeaks revealed how the Agency masks its hacking exploits, to make it appear another state actor was responsible. Dubbed ‘Marble Framework’, among other things the resource inserts foreign-language text into malware source codes to misdirect security analysts. The Framework can obfuscate in this manner via Arabic, Chinese, English, Farsi, Korean, and Russian.
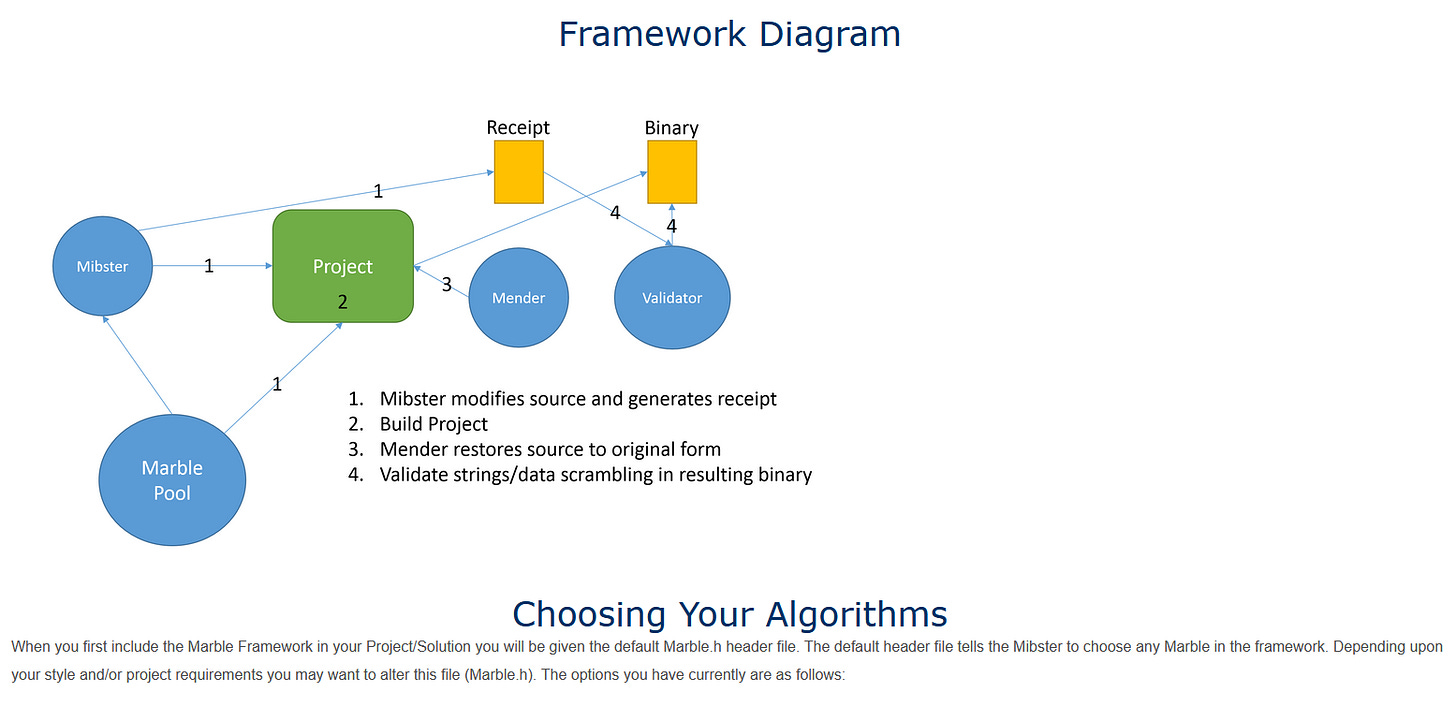
Excerpt from leaked Marble Framework files
Moreover, CIA hackers employ crafty tricks and double bluffs to reinforce these bogus attributions, such as creating the appearance of attempts to conceal foreign-language text. Thus, forensic investigators are successfully conned into concluding even more strongly that the country framed by Langley is responsible. Unbelievably, this seismic disclosure prompted no Western journalist to reappraise the widely received narrative that Moscow’s GRU was responsible for the hack and leak of damaging Democratic National Committee emails in 2016.
That conclusion, universally reinforced by the Western media, was initially peddled by Matt Tait, a former GCHQ spy. He didn’t base his conclusions on anything technical, but “basic operational security failures” he detected on the part of the individual(s) who released the communications, including their computer username referencing the founder of the Soviet Union’s secret police, and “ham-fisted” attempts to pose as Romanian. Which is, of course, precisely how the CIA would cover its own tracks via Marble Framework.
‘Irrevocable Proof’
There has similarly been no mainstream discussion of why the Agency would seek to acquire and maintain this capability in the first place. Now that NATO considers cyberattacks an Article 5 matter, this question has never been a more urgent question, given the CIA’s extensive and deplorable history of false-flag operations to overthrow governments, and kickstart conflicts.
For example, in April 1953, the CIA and MI6 launched a welter of covert actions to undermine Iranian Prime Minister Mohammad Mosaddegh, in order to lay the foundations of his ouster. One key tactic in which the pair engaged was bombing mosques, and homes of prominent Muslim figures by operatives posing as members of Tehran’s Communist Party. A subsequent internal review of the coup noted that this incendiary activity mobilised Mullahs to take action against Mosaddegh.
These efforts were judged to have contributed to the “positive outcome” of the wider coup effort. Such a glowing appraisal of these false flag manoeuvres may have informed the dimensions of Operation Northwoods, a daring set of proposals under which the CIA would stage and commit acts of terrorism against US military and civilian targets. These could then be blamed on the government of Fidel Castro, precipitating all-out war with Cuba.

Potential false-flag actions outlined in extraordinary declassified documents include assassinating of Cuban immigrants on US soil, sinking boats ferrying Cuban refugees to Florida, shooting down US civilian airlines, blowing up US ships, and more. One specific element of Operation Northwoods is particularly relevant to consider in light of alleged state cyberattacks becoming Article 5 worthy. If the 1962 Mercury launch – the first US orbital spaceflight – went awry, Castro would be blamed by concocting:
“Irrevocable proof… the fault lies with the Communists… this to be accomplished by manufacturing various pieces of evidence which would prove electronic interference on the part of the Cubans.”
While Northwoods was ultimately rejected by President John F. Kennedy, the US military and intelligence community continued constructing false-flag blueprints thereafter. In 1963, a Pentagon policy paper advocated making it appear that Cuba had attacked a member of the Organization of American States (OAS), justifying US retaliation:
“A contrived ‘Cuban’ attack on an OAS member could be set up, and the attacked state could be urged to take measures of self-defense and request assistance from the US and OAS.”
Langley’s cyberattack connivances have surely only grown more sophisticated, and more complex to unravel, in the years since Marble Framework was publicly exposed. Pinning blame on a foreign country for a cyberattack it didn’t actually commit is no doubt even easier and more effective today. Resultantly, a false flag tripwire for Beijing, Moscow, or any other Washington-mandated ‘enemy’ state to unwittingly and unwillingly stumble over, triggering the outbreak of global war, has now been forged by NATO.
Share this:
Related
July 16, 2024 - Posted by aletho | Deception, False Flag Terrorism, Timeless or most popular | CIA, NATO, United States
No comments yet.
This site uses Akismet to reduce spam. Learn how your comment data is processed.
Featured Video
The Sordid History of the CIA – Part 2
or go to
Aletho News Archives – Video-Images
From the Archives
Rabbi Shmuel Eliyahu: Leave No Palestinian or Arab Alive
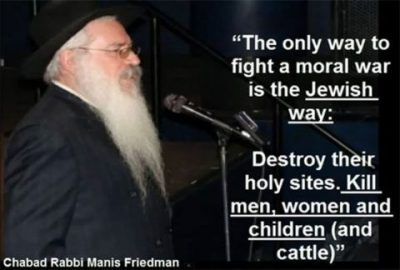
By Jonas E. Alexis | Veterans Today | July 23, 2017
Israeli Rabbi Shmuel Eliyahu seems to have picked up where the late Rabbi Ovadiah Yosef left off. The Israeli army, Eliyahu said, must slaughter the Palestinians “and leave no one alive.” The Palestinians, the good rabbi continued, must be “destroyed and crushed in order to end violence.” Here is Eliyahu’s algorithm:
“If they don’t stop after we kill 100, then we must kill 1,000. And if they do not stop after 1,000, then we must kill 10,000. If they still don’t stop we must kill 100,000, even a million.”
There is more to this “logic” than meets the eye and ear. Eliyahu even postulated that the Israeli army ought not to get involved in arresting Palestinians because “If you leave him alive, there is a fear that he will be released and kill other people. We must eradicate this evil from within our midst.”
You may say that this is just an isolated case. No Israeli official believes that, right? … continue
Blog Roll
-
Join 2,406 other subscribers
Visits Since December 2009
- 7,379,333 hits
Looking for something?
Archives
Calendar
Categories
Aletho News Civil Liberties Corruption Deception Economics Environmentalism Ethnic Cleansing, Racism, Zionism Fake News False Flag Terrorism Full Spectrum Dominance Illegal Occupation Mainstream Media, Warmongering Malthusian Ideology, Phony Scarcity Militarism Progressive Hypocrite Russophobia Science and Pseudo-Science Solidarity and Activism Subjugation - Torture Supremacism, Social Darwinism Timeless or most popular Video War Crimes Wars for IsraelTags
9/11 Afghanistan Africa al-Qaeda Australia BBC Benjamin Netanyahu Brazil Canada CDC Central Intelligence Agency China CIA CNN Covid-19 COVID-19 Vaccine Donald Trump Egypt European Union Facebook FBI FDA France Gaza Germany Google Hamas Hebron Hezbollah Hillary Clinton Human rights Hungary India Iran Iraq ISIS Israel Israeli settlement Japan Jerusalem Joe Biden Korea Latin America Lebanon Libya Middle East National Security Agency NATO New York Times North Korea NSA Obama Pakistan Palestine Poland Qatar Russia Sanctions against Iran Saudi Arabia Syria The Guardian Turkey Twitter UAE UK Ukraine United Nations United States USA Venezuela Washington Post West Bank WHO Yemen ZionismRecent Comments
 Aletho News
Aletho News- Jeffrey Epstein’s sinister shadow over West Asia
- The Sordid History of the CIA – Part 2
- French FM under fire over ‘false’ claims about UN rapporteur
- Israel Wants ISIS-Linked Militias To Control Rafah Crossing — The New Order in Gaza
- ISIS never left Syria, it just changed uniforms
- Why ARE the US and Israel Obsessed With Eliminating Iran’s Ballistic Missiles?
- Kremlin comments on EU ‘myopia’ over dialogue with Russia
- Russia more adapted to contemporary military technology than NATO
- Germany puts caveat on more missiles for Ukraine
- UK High Court rules Palestine Action ban unlawful
 If Americans Knew
If Americans Knew- Noor’s short life of unimaginable suffering
- Israel Destroyed Gaza’s Hospitals. Now It’s Banning Doctors Without Borders.
- Is Spite of What Zionists Say, It’s a Good Thing to Criticize Governments
- Palestinian mother, daughter recount strip searches, harsh conditions in Israeli detention
- Israel used weapons in Gaza that made thousands of Palestinians evaporate
- ADL’s Stats Twist Israel’s Critics Into Antisemites
- Why Is the World Silent When the Gaza Genocide Is Not Over?
- In Gaza: 8,000 bodies under rubble, 3,000 missing – Not a ceasefire Day 126
- AZAPAC, the new PAC opposing Israeli domination of U.S policies
- Haim Saban: Billionaire for Israel
 No Tricks Zone
No Tricks Zone- Unfudging The Data: Dutch Meteorological Institute Reinstates Early 20th Centruy Heat Waves It Had Erased Earlier
- German Gas Crisis…Chancellor Merz Allegedly Bans Gas Debate Ahead of Elections!
- Pollen Reconstructions Show The Last Glacial’s Warming Events Were Global, 10x Greater Than Modern
- Germany’s Natural Gas Storage Level Dwindles To Just 28%… Increasingly Critical
- New Study Rebuts The Assumption That Anthropogenic CO2 Molecules Have ‘Special’ Properties
- Climate Scientist Who Predicted End Of “Heavy Frost And Snow” Now Refuses Media Inquiries
- Polar Bear Numbers Rising And Health Improving In Areas With The Most Rapid Sea Ice Decline
- One Reason Only For Germany’s Heating Gas Crisis: Its Hardcore-Dumbass Energy Policy
- 130 Years Later: The CO2 Greenhouse Effect Is Still Only An Imaginary-World Thought Experiment
- New Study Affirms Rising CO2’s Greening Impact Across India – A Region With No Net Warming In 75 Years
Contact:
atheonews (at) gmail.com
Disclaimer
This site is provided as a research and reference tool. Although we make every reasonable effort to ensure that the information and data provided at this site are useful, accurate, and current, we cannot guarantee that the information and data provided here will be error-free. By using this site, you assume all responsibility for and risk arising from your use of and reliance upon the contents of this site.
This site and the information available through it do not, and are not intended to constitute legal advice. Should you require legal advice, you should consult your own attorney.
Nothing within this site or linked to by this site constitutes investment advice or medical advice.
Materials accessible from or added to this site by third parties, such as comments posted, are strictly the responsibility of the third party who added such materials or made them accessible and we neither endorse nor undertake to control, monitor, edit or assume responsibility for any such third-party material.
The posting of stories, commentaries, reports, documents and links (embedded or otherwise) on this site does not in any way, shape or form, implied or otherwise, necessarily express or suggest endorsement or support of any of such posted material or parts therein.
The word “alleged” is deemed to occur before the word “fraud.” Since the rule of law still applies. To peasants, at least.
Fair Use
This site contains copyrighted material the use of which has not always been specifically authorized by the copyright owner. We are making such material available in our efforts to advance understanding of environmental, political, human rights, economic, democracy, scientific, and social justice issues, etc. We believe this constitutes a ‘fair use’ of any such copyrighted material as provided for in section 107 of the US Copyright Law. In accordance with Title 17 U.S.C. Section 107, the material on this site is distributed without profit to those who have expressed a prior interest in receiving the included information for research and educational purposes. For more info go to: http://www.law.cornell.edu/uscode/17/107.shtml. If you wish to use copyrighted material from this site for purposes of your own that go beyond ‘fair use’, you must obtain permission from the copyright owner.
DMCA Contact
This is information for anyone that wishes to challenge our “fair use” of copyrighted material.
If you are a legal copyright holder or a designated agent for such and you believe that content residing on or accessible through our website infringes a copyright and falls outside the boundaries of “Fair Use”, please send a notice of infringement by contacting atheonews@gmail.com.
We will respond and take necessary action immediately.
If notice is given of an alleged copyright violation we will act expeditiously to remove or disable access to the material(s) in question.
All 3rd party material posted on this website is copyright the respective owners / authors. Aletho News makes no claim of copyright on such material.

Leave a comment