Whitney Webb is a MintPress News journalist based in Chile. She has contributed to several independent media outlets including Global Research, EcoWatch, the Ron Paul Institute and 21st Century Wire, among others. She has made several radio and television appearances and is the 2019 winner of the Serena Shim Award for Uncompromised Integrity in Journalism.
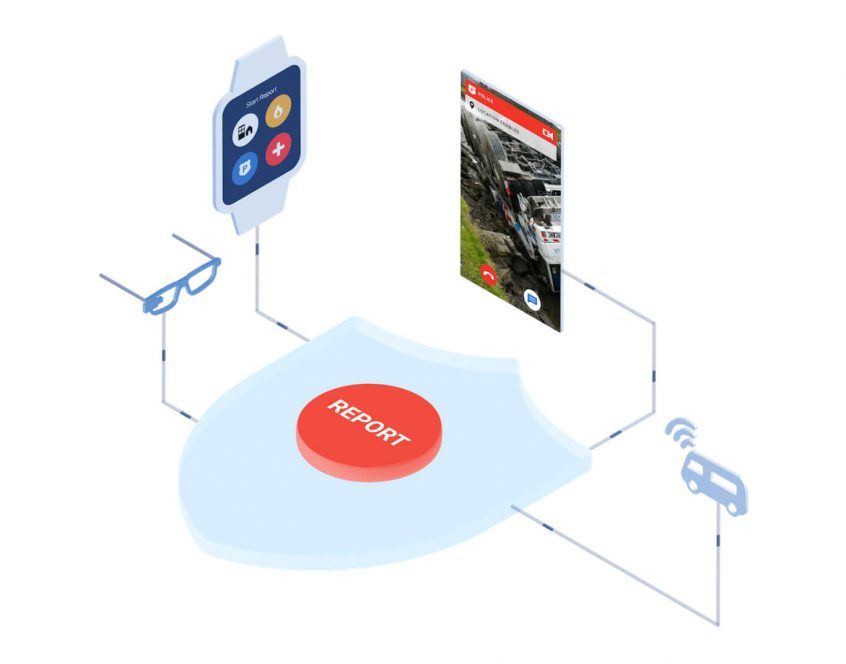
Newspapers: Fusion Centers Have Secretly Created A National Citizen Spying Program
MassPrivateI | August 6, 2020
 What has the public learned about Fusion Centers since the recent BlueLeaks hack was released over a month ago? Not a lot.
What has the public learned about Fusion Centers since the recent BlueLeaks hack was released over a month ago? Not a lot.
The Feds have done a great job of keeping the public from finding out what DHS Fusion/Intelligence Centers are really doing. In a country founded on freedom, we find federal and local law enforcement scrambling to keep the true function of Fusion Centers hidden from the public.
By piecing together news articles from Maine and Texas papers, a disturbing picture begins to unfold of warrantless surveillance of Americans.
The first proof that Fusion Centers were being used to spy on everyday citizens and activists can be found in a Maine Press Herald article from mid-July.
“A cache of internal police documents stolen from a secretive Maine State Police intelligence unit has provided the first substantial glimpse into how it collects and shares information about crime suspects and political activists and, in rare cases, keep tabs on domestic extremists, gang members and anti-government groups.”
The article goes into greater detail describing how local police use Fusion Centers to track down low-level offenders and ID people from social media or video footage.
“Police agencies commonly contact the Maine center with requests for help identifying a person depicted in a photo, sometimes captured from a surveillance camera. Other pictures are taken directly by law enforcement, or appear to be pulled from Facebook or other social media sites.”
Maine police even went so far as to ask the Fusion Center to identify a passenger in a car who refused to identify himself, and did not consent to having his photograph taken or his fingerprints scanned.
Another article in the Maine Press Herald which predated BlueLeaks, revealed that Fusion Centers refuse to acknowledge that they are secretly scanning everyone’s faces and spying on their cellphones.
“Despite evidence that the Maine State Police has worked for years with federal agencies to develop its use of digital surveillance technology, the agency now uses that law to refuse to answer any questions about such efforts, or even acknowledge that they exist.”
A third Maine Press Herald article revealed that Fusion Centers are secretly collecting a massive database of license plate numbers, the names and addresses of legal gun owners, and monitoring political activist groups and collecting members names and addresses.
The Austin Chronicle revealed that Fusion Centers have used secret informants to create a national “Suspicious Activity” network.
“In early June, an intelligence center operated by the Austin Police Department was hacked, along with many others like it across the country. Known as BlueLeaks, the collection of leaked documents from the hack contains over 10 gigs of material taken from the Austin center. They reveal a secret citizen spying program that’s active in the Austin area and across the country.”
The article reveals how Fusion Centers have created a vast network of secret “Threat Liaison Officers” (TLOs).
“Documents examined by the Chronicle show that each TLO must sign a nondisclosure agreement with ARIC, including those not working in law enforcement, essentially creating secret citizen officers.”
Secret citizen spies or TLOs could be someone you least expect. TLOs could be anyone: “private security officers with local hotels, malls, large venues, and local semiconductor companies. Government employees in “education,” “code enforcement,” and “public works” also contribute to ARIC as FOUO TLOs.
According to the article, TLOs could be teachers, trash collectors, ministers, priests, rabbi’s or even counselors.
Basically DHS has succeeded in creating a network of secret government spies masquerading as everyday people.
A TLOs job is to report people for doing mundane things like asking questions, taking pictures or being observant of one’s surroundings. TLOs are also reporting people for “suspicious” social media posts, whatever that means.
“According to one FOUO TLO’s report, an individual was seen taking photos of Zach Scott’s Topfer Theatre on Sept. 22, 2016. The report includes five different pictures of a young person using a camera on a tripod to photograph the theatre from across the street.”
To make it easier to report Americans for doing mundane things, Fusion Centers have provided TLOs with a checklist.
“The leaked documents include submission forms TLOs use to make their reports. At the top of the forms are boxes to check indicating the type of activity being reported. These include the aforementioned “School Threat,” but also Eliciting Information, Observation/Surveillance, and Suspicious/Odd Facebook Post. The TLO report spreadsheet contains 128 reports of school threats. But the category most reported by far was Expressed or Implied Threat, with more than a thousand entries.”
To say that this is reminiscent of China, the USSR or East Germany is an understatement. As the Chronicle warned, ‘worrisome examples of suspicious activity have led to increased scrutiny’ which means the Feds and local police could be secretly monitoring innocent Americans without out any public scrutiny.
If you thought DHS’s “If You See Something, Say Something” was a failure guess again. DHS has managed to justify creating 78 Fusion Centers whose sole purpose, it seems, is to spy on innocent Americans and track their daily movements.
Cybereason Announces New Plans to “Accelerate” Access to US Govt Networks Ahead of 2020 Election

By Whitney Webb | The Last American Vagabond | July 27, 2020
A cybersecurity firm tied to Israeli intelligence’s Unit 8200 that simulated a series of terrorist attacks occurring on the U.S. 2020 election has announced a new hire with deep ties to the U.S. intelligence and defense communities with the goal of gaining greater access to U.S. government networks.
A cybersecurity company tied to Israeli intelligence and a series of unnerving simulations regarding cyber-terrorist attacks on the upcoming U.S. elections has recently announced a new hire who plans to aid the company in further penetrating the U.S. public sector. Last Wednesday, the company Cybereason announced that it had hired Andrew Borene as its Managing Director for its recently launched U.S. public sector business. Borene, who boasts longstanding ties to the U.S. intelligence community and the Pentagon, “will accelerate Cybereason’s partner and customer presence in the U.S. public sector,” according to a Cybereason press release.
“My goal is to build a strong business for Cybereason within the U.S. public sector and I am planning to recruit a group of direct support executives, veterans and alumni of the elite [U.S.] military units and agencies that have defended our nation in the information age. I’ll also work to establish a network of the best channel and delivery partners for federal, state and local governments,” Borene said per the press release.
Eric Appel, Cybereason’s General Manager for North American Sales, stated that “We’re excited about Andrew joining Cybereason and the opportunity in the U.S. public sector for Cybereason to make a profound impact on helping the nation’s federal civilian, military, state and local government agencies…”
Borene will likely be successful in his ability to recruit a sales team of prominent alumni from the U.S. intelligence and defense communities to market Cybereason’s products throughout the U.S. government. Prior to joining Cybereason, Borene was a senior advisor to the Intelligence Advanced Research Projects Activity (IARPA), the intelligence community’s “DARPA” equivalent that is housed within the Office of the Director of National Intelligence (ODNI). He served in that capacity on behalf of intelligence contractor Booz Allen Hamilton. Prior to that, Borene served as Associate Deputy General Counsel to the Pentagon and was previously a military intelligence officer for the U.S. Marine Corps.
Borene’s private sector experience is also significant, as he was a senior executive at IBM. Notably, the current Chief Information Officer for the CIA, Juliane Gallina, had served alongside Borene as a top IBM executive prior to taking her current position at the agency. In addition, Borene also boasts ties to Wall Street as a veteran of Wells Fargo’s investment banking division.
In addition, Borene has deep ties to Washington’s foreign policy establishment as a “life member” of the Council on Foreign Relations (CFR) and to the national security-think tank nexus through his senior fellowship at the National Security Institute (NSI). NSI’s board includes former NSA directors, Keith Alexander and Michael Hayden (also a former CIA director); former Deputy Defense Secretary and “architect” of the Iraq War, Paul Wolfowitz; former director of the Defense Intelligence Agency, David Shedd; and a variety of other former top intelligence and defense officials as well as Silicon Valley executives and venture capitalists.
Notably, Borene is the latest addition to Cybereason with ties to the U.S. intelligence and defense communities as the company’s advisors include Robert Bigman, former Chief Information Security Officer for the CIA as well as Peter Sherlock, the former Chief Operating Officer of MITRE corporation, a major intelligence and defense contractor connected to the Ptech-9/11 controversy.
Cybereason: a front for Israeli Military Intelligence
Cybereason’s announcement of its hire of Andrew Borene coincided with its launch of its new “U.S. public sector business,” meaning that Cybereason now seeks to have its cybersecurity software running on even more of the U.S. government’s most classified networks. Cybereason, for years, has already been running on several sensitive U.S. government networks through its partnerships with IT contractors for intelligence and defense, such as Lockheed Martin (also a Cybereason investor), WWT and Leidos. However, Borene’s hire and this new publicly announced pivot towards the U.S. public sector clearly demonstrates the company’s interest in further deepening its presence on U.S. government networks.
Cybereason’s pivot is concerning for several reasons. First, its co-founders are alumni of Israel’s Unit 8200, an elite unit of the Israeli Intelligence corps that is part of the IDF’s Directorate of Military Intelligence and is involved mainly in signal intelligence, surveillance, cyberwarfare and code decryption. It is also well-known for its surveillance of Palestinian civilians and for using intercepted communications as blackmail in order to procure informants among Palestinians living under occupation in the West Bank.
In addition, all three Cybereason co-founders, after leaving Unit 8200, went on to work for two private Israel-based tech/telecom companies with a notorious history of aggressive espionage against the U.S. government: Amdocs and Comverse Infosys (the latter is now known as Verint Systems Inc.). This raises the possibility that Cybereason software could potentially be used as a backdoor by unauthorized actors, given that the company’s co-founders all previously worked for firms that have a history of placing backdoors into U.S. telecommunications and electronic infrastructure as well as aggressively spying on U.S. federal agencies.
Also notable is the fact that the company’s current CEO and co-founder Lior Div was much more than the average Unit 8200 officer during his time in the unit, as he “served as a commander [in Unit 8200] and carried out some of the world’s largest cyber offensive campaigns against nations and cybercrime groups. For his achievements, he received the Medal of Honor, the highest honor bestowed upon Unit 8200 members,” according to his biography. Troublingly, in an interview that Div gave to TechCrunch last year, Div stated that his work at Cybereason is “the continuation of the six years of training and service he spent working with the Israeli army’s 8200 Unit.”
This is particularly noteworthy given that Israel’s government has openly admitted that an on-going intelligence operation, first initiated in 2012 – the year Cybereason was founded, involves Israeli military intelligence and intelligence operations that had previously done “in house” (i.e. as part of Unit 8200, Mossad, etc.) being spun off into private companies, specifically start-ups in the “cyber” realm.
This operation is part of Israeli Prime Minister Benjamin Netanyahu’s “deliberate policy” to have former members of Israel’s “military and intelligence units … merge into companies with local partners and foreign partners” in order to make it all but impossible for major corporations and foreign governments to boycott Israel and to also to ensure that Israel becomes the world’s dominant “cyber power.”
One notable report on this policy, published by Israeli outlet Calcalist Tech, interviewed dozens of Israeli military, intelligence and government officials and noted that “since 2012, cyber-related and intelligence projects that were previously carried out in-house in the Israeli military and Israel’s main intelligence arms are transferred to companies that in some cases were built for this exact purpose.” The article also states that beginning in 2012, Israel’s intelligence and military intelligence agencies began to outsource “activities that were previously managed in-house, with a focus on software and cyber technologies.”
“Simulating” the Cancellation of the 2020 Election
In light of Cybereason’s background and the “acceleration” of their presence on U.S. government networks, the timing of their redoubled efforts to court the U.S. public sector add additional layers of concern given that it precedes the U.S. 2020 election by a matter of months. Since last year, Cybereason has conducted multiple simulations focused on the 2020 election, which were attended by federal officials from the FBI, DHS and the U.S. Secret Service and all of which ended in disaster. In those simulations, the 2020 election was ultimately canceled and martial law was then declared due to the chaos created by a group of hackers led by Cybereason employees.
Notably, Cybereason stood to gain nothing financially from the simulations given that their software could not have prevented the attacks waged against the U.S.’ electoral infrastructure in the exercise and the company framed their hosting of the simulations as merely “altruistic” because of their professed desire to help “protect” U.S. election infrastructure. The attacks conducted in the simulations by Cybereason employees included creating power grid blackouts, the use of deep fakes to sow confusion, creating havoc with municipal sewage systems and crashing self-driving cars into voters waiting in line to cast their ballots, killing 32 and injuring over a hundred people.
In the months since I first wrote about Cybereason and their 2020 “doomsday” simulations back in January, U.S. government officials and mass media alike have been warning that these same types of attacks that Cybereason simulated are likely to come to pass on this upcoming election day, scheduled for November 3rd of this year. More recently, in less than a week, headlines like “Election Security Experts Expect ‘Chaos’ Unless Action Taken,” “New York’s Pandemic Voting ‘Chaos’ Set to Go Nationwide in November,” and “Foreign adversaries ‘seeking to compromise’ presidential campaigns, intel warns,” among others, have been published in major U.S. media outlets.
While these narratives have asserted that China, Russia and/or Iran will be to blame for such attacks, it is worth noting that a tight-knit web of Israeli state-owned and private companies tied to Israeli military intelligence now run the software controlling key parts of the power grid in New York, California and elsewhere in the U.S.; are the main global producers of deep fakes; and the main providers of “security” software for self-driving and semi-self-driving cars, the quantity of which on U.S. streets has grown dramatically as a result of the coronavirus crisis.
With Cybereason’s newly announced push to run its software on critical U.S. government networks at both the federal and state levels, the company’s history of simulating terror attacks on critical U.S. infrastructure and their openly admitted and on-going ties to Israeli military intelligence deserve more scrutiny than ever as the U.S. election draws closer.
How an Israeli Spy-Linked Tech Firm Gained Access to the US Gov’t’s Most Classified Networks

By Whitney Webb |
Unlimited Hangout| July 15, 2020
If the networks of the U.S. military, the U.S. intelligence community and a slew of other U.S. federal agencies were running the software of a company with deep ties, not only to foreign companies with a history of espionage against the U.S. but also foreign military intelligence, it would — at the very least — garner substantial media attention. Yet, no media reports to date have noted that such a scenario exists on a massive scale and that the company making such software recently simulated the cancellation of the 2020 election and the declaration of martial law in the United States.
Earlier this month, MintPress News reported on the simulations for the U.S. 2020 election organized by the company Cybereason, a firm led by former members of Israel’s military intelligence Unit 8200 and advised by former top and current officials in both Israeli military intelligence and the CIA. Those simulations, attended by federal officials from the FBI, DHS and the U.S. Secret Service, ended in disaster, with the elections ultimately canceled and martial law declared due to the chaos created by a group of hackers led by Cybereason employees.
The first installment of this three part series delved deeply into Cybereason’s ties to the intelligence community of Israel and also other agencies, including the CIA, as well as the fact that Cybereason stood to gain little financially from the simulations given that their software could not have prevented the attacks waged against the U.S.’ electoral infrastructure in the exercise.
Also noted was the fact that Cybereason software could be potentially used as a backdoor by unauthorized actors, a possibility strengthened by the fact that the company’s co-founders all previously worked for firms that have a history of placing backdoors into U.S. telecommunications and electronic infrastructure as well as aggressive espionage targeting U.S. federal agencies.
The latter issue is crucial in the context of this installment of this exclusive MintPress series, as Cybereason’s main investors turned partners have integrated Cybereason’s software into their product offerings. This means that the clients of these Cybereason partner companies, the U.S. intelligence community and military among them, are now part of Cybereason’s network of more than 6 million endpoints that this private company constantly monitors using a combination of staff comprised largely of former intelligence operatives and an AI algorithm first developed by Israeli military intelligence.
Cybereason, thus far, has disclosed the following groups as lead investors in the company: Charles River Ventures (CRV), Spark Capital, Lockheed Martin and SoftBank. Charles River Ventures (CRV) was among the first to invest in Cybereason and has been frequently investing in other Israeli tech start-upsthat were founded by former members of the elite Israeli military intelligence Unit 8200 over the last few years. Spark Capital, based in California, appears to have followed CRV’s interest in Cybereason since the venture capitalist who co-founded Spark and led its investment in Cybereason is a former CRV partnerwho still has close ties to the firm.
While CRV and Spark Capital seem like just the type of investors a company like Cybereason would attract given their clear interest in similar tech start-ups coming out of Israel’s cyber sector, Cybereason’s other lead investors — Lockheed Martin and SoftBank — deserve much more attention and scrutiny.
Cybereason widely used by US Government, thanks to Lockheed
“A match made in heaven,” trumpeted Forbes at the news of the Lockheed Martin-Cybereason partnership, first forged in 2015. The partnership involved not only Lockheed Martin becoming a major investor in the cybersecurity company but also in Lockheed Martin becoming the largest conduit providing Cybereason’s software to U.S. federal and military agencies.
Indeed, as Forbes noted at the time, not only did Lockheed invest in the company, it decided to integrate Cybereason’s software completely into its product portfolio, resulting in a “model of both using Cybereason internally, and selling it to both public and private customers.”
Cybereason CEO and former offensive hacker for Israeli military intelligence — Lior Div — said the following of the partnership:
Lockheed Martin invested in Cybereason’s protection system after they compared our solution against a dozen others from the top industry players. The US firm was so impressed with the results they got from Cybereason that they began offering it to their own customers – among them most of the top Fortune 100 companies, and the US federal government. Cybereason is now the security system recommended by LM to its customers for protection from a wide (sic) malware and hack attacks.”
Rich Mahler, then-director of Commercial Cyber Services at Lockheed Martin, told Defense Daily that the company’s decision to invest in Cybereason, internally use its software, and include the technology as part of Lockheed Martin’s cyber solutions portfolio were all “independent business decisions but were all coordinated and timed with the transaction.”
How independent each of those decisions actually was is unclear, especially given the timing of Lockheed Martin’s investment in Cybereason, whose close and troubling ties to Israeli intelligence as well as the CIA were noted in the previous installment of this investigative series. Indeed, about a year prior to their investment in the Israeli military intelligence-linked Cybereason, Lockheed Martin opened an office in Beersheba, Israel, where the IDF has its “cyberhub”. The office is focused not on the sales of armaments, but instead on technology.
Marilyn Hewson, Lockheed Martin’s CEO, said the following during her speech that inaugurated the company’s Beersheba office:
The consolidation of IDF Technical Units to new bases in the Negev Desert region is an important transformation of Israel’s information technology capability… We understand the challenges of this move. Which is why we are investing in the facilities and people that will ensure we are prepared to support for these critical projects. By locating our new office in the capital of the Negev we are well positioned to work closely with our Israeli partners and stand ready to: accelerate project execution, reduce program risk and share our technical expertise by training and developing in-country talent.”
Beersheba not only houses the IDF’s technology campus, but also the Israel National Cyber Directorate, which reports directly to Israel’s Prime Minister, as well as a high-tech corporate park that mostly houses tech companies with ties to Israel’s military intelligence apparatus. The area has been cited in several media reports as a visible indicator of the public-private merger between Israeli technology companies, many of them started by Unit 8200 alumni, and the Israeli government and its intelligence services. Lockheed Martin quickly became a key fixture in the Beersheba-based cyberhub.
Not long before Lockheed began exploring the possibility of opening an office in Beersheba, the company was hacked by individuals who used tokens tied to the company, RSA Security, whose founders have ties to Israel’s defense establishment and which is now owned by Dell, a company also deeply tied to the Israeli government and tech sector. The hack, perpetrated by still unknown actors, may have sparked Lockheed’s subsequent interest in Israel’s cybersecurity sector.
Soon after opening its Beersheba office, Lockheed Martin created its Israel subsidiary, Lockheed Martin Israel. Unlike many of the company’s other subsidiaries, this one is focused exclusively on “cybersecurity, enterprise information technology, data centers, mobile, analytics and cloud” as opposed to the manufacture and design of armaments.
Haden Land, then-vice president of research and technology for Lockheed Martin, told the Wall Street Journal that the creation of the subsidiary was largely aimed at securing contracts with the IDF and that the company’s Israel subsidiary would soon be seeking partnership and investments in pursuit of that end. Land oversaw the local roll-out of the company’s Israel subsidiary while concurrently meeting with Israeli government officials. According to the Journal, Land “oversees all of Lockheed Martin’s information-systems businesses, including defense and civilian commercial units” for the United States and elsewhere.
Just a few months later, Lockheed Martin partnered and invested in Cybereason, suggesting that Lockheed’s decision to do so was aimed at securing closer ties with the IDF. This further suggests that Cybereason still maintains close ties to Israeli military intelligence, a point expounded upon in great detail in the previous installment of this series.
Thus, it appears that not only does Lockheed Martin use Cybereason’s software on its own devices and on those it manages for its private and public sector clients, but it also decided to use the company’s software in this way out of a desire to more closely collaborate with the Israeli military in matters related to technology and cybersecurity.
The cozy ties between Lockheed Martin, one of the U.S. government’s largest private contractors, and the IDF set off alarm bells, then and now, for those concerned with U.S. national security. Such concern makes it important to look at the extent of Cybereason’s use by federal and military agencies in the United States through their contracting of Lockheed Martin’s Information Technology (IT) division. This is especially important considering Israeli military intelligence’s history of using espionage, blackmail and private tech companies against the U.S. government, as detailed here.
While the exact number of U.S. federal and military agencies using Cybereason’s software is unknown, it is widespread, with Lockheed Martin’s IT division as the conduit. Indeed, Lockheed Martin was the number one IT solutions provider to the U.S. federal government up until its IT division was spun off and merged with Leidos Holdings. As a consequence, Leidos is now the largest IT provider to the U.S. government and is also directly partnered with Cybereason in the same way Lockheed Martin was. Even after its IT division was spun off, Lockheed Martin continues to use Cybereason’s software in its cybersecurity work for the Pentagon and still maintains a stake in the company.
The Leidos-Lockheed Martin IT hybrid provides a litany of services to the U.S. military and U.S. intelligence. As investigative journalist Tim Shorrock noted for The Nation, the company does “everything from analyzing signals for the NSA to tracking down suspected enemy fighters for US Special Forces in the Middle East and Africa” and, following its merger with Lockheed and consequential partnership with Cybereason, became “the largest of five corporations that together employ nearly 80 percent of the private-sector employees contracted to work for US spy and surveillance agencies.” Shorrock also notes that these private-sector contractors now dominate the mammoth U.S. surveillance apparatus, many of them working for Leidos and — by extension — using Cybereason’s software.
Leidos’ exclusive use of Cybereason software for cybersecurity is also relevant for the U.S. military since Leidos runs a number of sensitive systems for the Pentagon, including its recently inked contract to manage the entire military telecommunications infrastructure for Defense Information Systems Agency (DISA). In addition to maintaining the military telecom network, Cybereason is also directly partnered with World Wide Technologies (WWT) as of this past October. WWT manages cybersecurity for the U.S. Army, maintains DISA’s firewalls and data storage as well as the U.S. Air Force’s biometric identification system. WWT also manages contracts for NASA, itself a frequent target of Israeli government espionage, and the U.S. Navy. WWT’s partnership is similar to the Lockheed/Leidos partnership in that Cybereason’s software is now completely integrated into its portfolio, giving the company full access to the devices on all of these highly classified networks.
Many of these new partnerships with Cybereason, including its partnership with WWT, followed claims made by members of Israel’s Unit 8200 in 2017 that the popular antivirus software of Kaspersky Labs contained a backdoor for Russian intelligence, thereby compromising U.S. systems. The Wall Street Journal was the first to report on the alleged backdoor but did not mention the involvement of Unit 8200 in identifying it, a fact revealed by the New York Times a week later.
Notably, none of the evidence Unit 8200 used to blame Kaspersky has been made public and Kaspersky noted that it was actually Israeli hackers that had been discovered planting backdoors into its platform prior to the accusation levied against Kaspersky by Unit 8200. As the New York Times noted:
Investigators later discovered that the Israeli hackers had implanted multiple back doors into Kaspersky’s systems, employing sophisticated tools to steal passwords, take screenshots, and vacuum up emails and documents.”
Unit 8200’s claims ultimately led the U.S. government to abandon Kaspersky’s products entirely in 2018, allowing companies like Cybereason (with its own close ties to Unit 8200) to fill the void. Indeed, the very agencies that banned Kaspersky now use cybersecurity software that employs Cybereason’s EDR system. No flags have been raised about Cybereason’s own collaboration with the very foreign intelligence service that first pointed the finger at Kaspersky and that previously sold software with backdoors to sensitive U.S. facilities.
SoftBank, Cybereason and the Vision Fund
While its entry into the U.S. market and U.S. government networks is substantial, Cybereason’s software is also run throughout the world on a massive scale through partnerships that have seen it enter into Latin American and European markets in major ways in just the last few months. It has also seen its software become prominent in Asia following a partnership with the company Trustwave. Much of this rapid expansion followed a major injection of cash courtesy of one of the company’s biggest clients and now its largest investor, Japan’s SoftBank.
SoftBank first invested in Cybereason in 2015, the same year Lockheed Martin initially invested and partnered with the firm. It was also the year that SoftBank announced its intention to invest in Israeli tech start-ups. SoftBank first injected $50 million into Cybereason, followed by an additional $100 million in 2017 and $200 million last August. SoftBank’s investments account for most of the money raised by the company since it was founded in 2012 ($350 million out of $400 million total).
Prior to investing, Softbank was a client of Cybereason, which Ken Miyauchi, president of SoftBank, noted when making the following statement after Softbank’s initial investment in Cybereason:
SoftBank works to obtain cutting edge technology and outstanding business models to lead the Information Revolution. Our deployment of the Cybereason platform internally gave us firsthand knowledge of the value it provides, and led to our decision to invest. I’m confident Cybereason and SoftBank’s new product offering will bring a new level of security to Japanese organizations.”
SoftBank — one of Japan’s largest telecommunications companies — not only began to deploy Cybereason internally but directly partnered with it after investing, much like Lockheed Martin had done around the same time. This partnership resulted in SoftBank and Cybereason creating a joint venture in Japan and Cybereason creating partnerships with other tech companies acquired by SoftBank, including the U.K.’s Arm, which specializes in making chips and management platforms for Internet of Things (IoT) devices.
SoftBank’s interest in Cybereason is significant, particularly in light of Cybereason’s interest in the 2020 U.S. election, given that SoftBank has significant ties to key allies of President Trump and even the president himself.
Indeed, SoftBank’s Masayoshi Son was among the first wave of international business leaders who sought to woo then-president-elect Trump soon after the 2016 election. Son first visited Trump Tower in December 2016 and announced, with Trump by his side in the building’s lobby, that SoftBank would invest $50 billion in the U.S. and create 50,000 jobs. Trump subsequently claimed on Twitter that Son had only decided to make this investment because Trump had won the election.
Son told reporters at the time that the investment would come from a $100 billion fund that would be created in partnership with Saudi Arabia’s sovereign wealth fund as well as other investors. “I just came to celebrate his new job. I said, ‘This is great. The US will become great again,’” Son said, according to reports.
Then, in March of 2017, Son sent top SoftBank executives to meet with senior members of Trump’s economic team and, according to the New York Times, “the SoftBank executives said that because of a lack of advanced digital investments, the competitiveness of the United States economy was at risk. And the executives made the case, quite strongly, that Mr. Son was committed to playing a major role in addressing this issue through a spate of job-creating investments.” Many of SoftBank’s investments and acquisitions in the U.S. since then have focused mainly on artificial intelligence and technology with military applications, such as “killer robot” firm Boston Dynamics, suggesting Son’s interest lies more in dominating futuristic military-industrial technologies than creating jobs for the average American.
After their initial meeting, Trump and Son met again a year later in June 2018, with Trump stating that “His [Son’s] $50 billion turned out to be $72 billion so far, he’s not finished yet.” Several media reports have claimed that Son’s moves since Trump’s election have sought to “curry favor” with the President.
Through the creation of this fund alongside the Saudis, SoftBank has since become increasingly intertwined with Saudi Crown Prince Muhammad bin Salman (MBS), a key ally of President Trump in the Middle East known for his authoritarian crackdowns on Saudi elites and dissidents alike. The ties between Saudi Arabia and SoftBank became ever tighter when MBS took the reins in the oil kingdom and after SoftBank announced the launch of the Vision Fund in 2016. SoftBank’s Vision Fund is a vehicle for investing in hi-tech companies and start-ups and its largest shareholder is the Public Investment Fund of Saudi Arabia. Notably, Son decided to launch the Vision Fund in Riyadh during President Trump’s first official visit to the Gulf Kingdom.
In addition, the Mubadala Investment Company, a government fund of the United Arab Emirates (UAE), gave $15 billion to the Vision Fund. UAE leadership also share close ties to the Trump administration and MBS in Saudi Arabia.
As a consequence, SoftBank’s Vision Fund is majority funded by two Middle Eastern authoritarian governments with close ties to the U.S. government, specifically the Trump administration. In addition, both countries have enjoyed the rapid growth and normalization of ties with the state of Israel in recent years, particularly following the rise of current Saudi Crown Prince Muhammad bin Salman and Jared Kushner’s rise to prominence in his father-in-law’s administration. Other investments in the Vision Fund have come from Apple, Qualcomm and Oracle’s Larry Ellison, all tech companies with strong ties to Israel’s government.
The Saudi and Emirati governments’ links to the Vision Fund are so obvious that even mainstream outlets like the New York Times have described them as a “front for Saudi Arabia and perhaps other countries in the Middle East.”
SoftBank also enjoys close ties to Jared Kushner, with Fortress Investment Group lending $57 million to Kushner Companies in October 2017 while it was under contract to be acquired by SoftBank. As Barron’s noted at the time:
When SoftBank Group bought Fortress Investment Group last year, the Japanese company was buying access to a corps of seasoned investors. What SoftBank also got is a financial tie to the family of President Donald Trump’s senior advisor and son-in-law, Jared Kushner.”
According to The Real Deal, Kushner Companies obtained the financing from Fortress only after its attempts to obtain funding through the EB-5 visa program for a specific real estate venture were abandoned after the U.S. Attorney and the Securities and Exchange Commission began to investigate how Kushner Companies used the EB-5 investor visa program. A key factor in the opening of that investigation was Kushner Companies’ representatives touting Jared Kushner’s position at the White House when talking to prospective investors and lenders.
SoftBank also recently came to the aid of a friend of Jared Kushner, former CEO of WeWork Adam Neumann. Neumann made shocking claims about his ties to both Kushner and Saudi Arabia’s MBS, even asserting that he had worked with both in creating Kushner’s long-awaited and controversial Middle East “peace plan” and claimed that he, Kushner and MBS would together “save the world.” Neumann previously called Kushner his “mentor.” MBS has also discussed on several occasions his close ties with Kushner and U.S. media reports have noted the frequent correspondence between the two “princelings.”
Notably, SoftBank invested in Neumann’s WeWork using money from the Saudi-dominated Vision Fund and later went on to essentially bail the company out after its IPO collapse and Neumann was pushed out. SoftBank’s founder, Masayoshi Son, had an odd yet very close relationship with Neumann, perhaps explaining why Neumann was allowed to walk with $1.7 billion after bringing WeWork to the brink of collapse. Notably, nearly half of SoftBank’s approximately $47 billion investments in the U.S. economy since Trump’s election, went to acquiring and then bailing out WeWork. It is unlikely that such a disastrous investment resulted in the level of job creation that Son had promised Trump in 2016.
Given that it is Cybereason’s top investor and shareholder by a large margin, SoftBank’s ties to the Trump administration and key allies of that administration are significant in light of Cybereason’s odd interest in 2020 U.S. election scenarios that end with the cancellation of this year’s upcoming presidential election. It goes without saying that the cancellation of the election would mean a continuation of the Trump administration until new elections would take place.
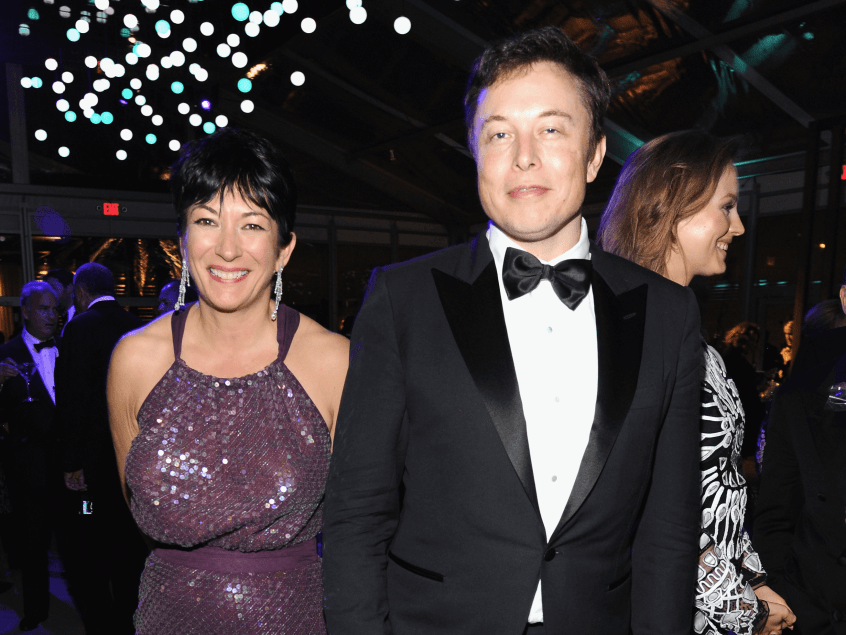
Furthermore, with Cybereason’s close and enduring ties to Israeli military intelligence now well-documented, it is worth asking if Israeli military intelligence would consider intervening in 2020 if the still-to-be-decided Democratic contender was strongly opposed to Israeli government policy, particularly Israel’s military occupation of Palestine. This is especially worth considering given revelations that sexual blackmailer and pedophile Jeffrey Epstein, who targeted prominent U.S. politicians, mostly Democrats, was in the employ of Israeli military intelligence.
Notably, Cybereason’s doomsday election scenarios involved the weaponization of deep fakes, self-driving cars and hacking Internet of Things devices, with all of those technologies being pioneered and perfected — not by Russia, China or Iran — but by companies directly tied to Israeli intelligence, much like Cybereason itself. These companies, their technology and Cybereason’s own work creating the narrative that U.S. rival states seek to undermine the U.S. election in this way, will all be discussed in the conclusion of MintPress’ series on Cybereason and its outsized interest in the U.S. democratic process.
Seth Rich, Julian Assange and Dana Rohrabacher – Will We Ever Know the Truth About the Stolen DNC Files?

Seth Rich, Julian Assange and Dana Rohrabacher. Credit: Public domain/Gage Skidmore/ Flickr
By Philip Giraldi | American Herald Tribune | February 29, 2020
The media is doing its best to make the story go away, but it seems to have a life of its own, possibly due to the fact that the accepted narrative about how Rich died makes no sense. In its Iatest manifestation, it provides an alternative explanation for just how the information from the Democratic National Committee (DNC) computer somehow made its way to Wikileaks. If you believe that Jeffrey Epstein committed suicide and that he was just a nasty pedophile rather than an Israeli intelligence agent, read no farther because you will not be interested in Rich. But if you appreciate that it was unlikely that the Russians were behind the stealing of the DNC information you will begin to understand that other interested players must have been at work.
For those who are not familiar with it, the backstory to the murder of apparently disgruntled Democratic National Committee staffer Seth Rich, who some days before may have been the leaker of that organization’s confidential emails to Wikileaks, suggests that a possibly motiveless crime might have been anything but. The Washington D.C. police investigated what they believed to be an attempted robbery gone bad but that theory fails to explain why Rich’s money, credit cards, cell phone and watch were not taken. Wikileaks has never confirmed that Rich was their source in the theft of the proprietary emails that had hitherto been blamed on Russia but it subsequently offered a $20,000 reward for information leading to resolution of the case and Julian Assange, perhaps tellingly, has never publicly clarified whether Rich was or was not one of his contacts, though there is at least one report that he confirmed the relationship during a private meeting.
Answers to the question who exactly stole the files from the DNC server and the emails from John Podesta have led to what has been called Russiagate, a tale that has been embroidered upon and which continues to resonate in American politics. At this point, all that is clearly known is that in the Summer of 2016 files and emails pertaining to the election were copied and then made their way to WikiLeaks, which published some of them at a time that was damaging to the Clinton campaign. Those who are blaming Russia believe that there was a hack of the Democratic National Committee (DNC) server and also of John Podesta’s emails that was carried out by a Russian surrogate or directly by Moscow’s military intelligence arm. They base their conclusion on a statement issued by the Department of Homeland Security on October 7, 2016, and on a longer assessment prepared by the Office of the Director of National Intelligence on January 6, 2017. Both government appraisals implied that there was a U.S. government intelligence agency consensus that there was a Russian hack, though they provided little in the way of actual evidence that that was the case and, in particular, failed to demonstrate how the information was obtained and what the chain of custody was as it moved from that point to the office of WikiLeaks. The January report was particularly criticized as unconvincing, rightly so, because the most important one of its three key contributors, the National Security Agency, had only moderate confidence in its conclusions, suggesting that whatever evidence existed was far from solid.
An alternative view that has been circulating for several years suggests that it was not a hack at all, that it was a deliberate whistleblower-style leak of information carried out by an as yet unknown party, possibly Rich, that may have been provided to WikiLeaks for possible political reasons, i.e. to express disgust with the DNC manipulation of the nominating process to damage Bernie Sanders and favor Hillary Clinton.
There are, of course, still other equally non-mainstream explanations for how the bundle of information got from point A to point B, including that the intrusion into the DNC server was carried out by the CIA which then made it look like it had been the Russians as perpetrators. And then there is the hybrid point of view, which is essentially that the Russians or a surrogate did indeed intrude into the DNC computers but it was all part of normal intelligence agency probing and did not lead to anything. Meanwhile and independently, someone else who had access to the server was downloading the information, which in some fashion made its way from there to WikiLeaks.
Both the hack vs. leak viewpoints have marshaled considerable technical analysis in the media to bolster their arguments, but the analysis suffers from the decidedly strange fact that the FBI never even examined the DNC servers that may have been involved. The hack school of thought has stressed that Russia had both the ability and motive to interfere in the election by exposing the stolen material while the leakers have recently asserted that the sheer volume of material downloaded indicates that something like a higher speed thumb drive was used, meaning that it had to be done by someone with actual physical direct access to the DNC system. Someone like Seth Rich.
What the many commentators on the DNC server issue choose to conclude is frequently shaped by their own broader political views, producing a result that favors one approach over another depending on how one feels about Trump or Clinton. Or the Russians. Perhaps it would be clarifying to regard the information obtained and transferred as a theft rather than either a hack or a leak since the two expressions have taken on a political meaning of their own in the Russiagate context. With all the posturing going on, the bottom line is that the American people and government have no idea who actually stole the material in question, though the Obama Administration was extraordinarily careless in its investigation and Russian President Vladimir Putin has generally speaking been blamed for what took place.
The story currently bouncing around the media concerns an offer allegedly made in 2017 by former Republican Congressman Dana Rohrabacher to imprisoned WikiLeaks founder Julian Assange. According to Assange’s lawyers, Rohrabacher offered a pardon from President Trump if Assange were to provide information that would attribute the theft or hack of the Democratic National Committee emails to someone other than the Russians. He was presumably referring to Seth Rich.
Assange did not accept the offer, but it should be noted that he has repeatedly stated in any event that he did not obtain the material from a Russian or Russian-linked source. In reality, he might not know the original source of the information. Since Rohrabacher’s original statement, both he and Trump have denied any suggestion that there was a firm offer with a quid pro quo for Assange. Trump claims to hardly know Rohrabacher and also asserts that he has never had a one-on-one meeting with him.
The U.S. media’s coverage of the story has emphasized that Assange’s cooperation would have helped to absolve Russia from the charge of having interfered decisively in the U.S. election, but the possible motive for doing so remains unclear. Russian-American relations are at their lowest point since the Cold War and that has largely been due to policies embraced by Donald Trump, to include the cancellation of START and medium range missile agreements. Trump has also approved NATO military maneuvers and exercises right up to the Russian border and has provided lethal weapons to Ukraine, something that his predecessor Barack Obama balked at. He has also openly confronted the Russians in Syria.
Given all of that back story, it would be odd to find Trump making an offer that focuses only on one issue and does not actually refute the broader claims of Russian interference, which are based on a number of pieces of admittedly often dubious evidence, not just the Clinton and Podesta emails. Which brings the tale back to Seth Rich. If Rich was indeed responsible for the theft of the information and was possibly killed for his treachery, it most materially impacts on the Democratic Party as it reminds everyone of what the Clintons and their allies are capable of. It will also serve as a warning of what might be coming at the Democratic National Convention in Milwaukee in July as the party establishment uses fair means or foul to stop Bernie Sanders. How this will all play out is anyone’s guess, but many of those who pause to observe the process will be thinking of Seth Rich.
Philip M. Giraldi is a former CIA counter-terrorism specialist and military intelligence officer who served nineteen years overseas in Turkey, Italy, Germany, and Spain. He was the CIA Chief of Base for the Barcelona Olympics in 1992 and was one of the first Americans to enter Afghanistan in December 2001. Phil is Executive Director of the Council for the National Interest, a Washington-based advocacy group that seeks to encourage and promote a U.S. foreign policy in the Middle East that is consistent with American values and interests.
DHS Head Claims Russia Seeks to ‘Undermine American Way of Life’, Expects US 2020 Voter Interference
Sputnik – 18.01.2020
Acting Secretary of the US Department of Homeland Security (DHS) Chad Wolf has joined the ranks of US officials who observe the DC political creed that Russia interferes in US internal affairs.
Wolf, in his 17 January speech, most of which was dedicated to what he referred to as the “top threats facing the Homeland” – Iran, China and Russia, claimed that even though Moscow does not strive to diminish the US role in the international arena, the nation is nonetheless looking to disrupt and undermine the “American way of life”.
“Lastly, let me touch on Russia. Unlike China, Russia doesn’t seek to weaken our economy and surpass us on the world-stage; rather they focus on actions that disrupt and undermine the American way of life. As we saw in 2016, we fully expect Russia to attempt to interfere in the 2020 elections to sow public discord and undermine our democratic institutions”, Wolf, serving as DHS acting secretary since November 2019, said, during an event hosted by the Homeland Security Experts Group in Washington DC.The official claimed that the 2018 midterm elections were “the most secure elections in the modern era” as the US created “classified and unclassified election war rooms” that “connected election officials in all 50 states, political parties, social media companies and agencies across the US Government, including DOD, the FBI and the Intelligence Community”.
“Let me be clear: We are prepared,” Wolf said. “More importantly, the state and local officials who run our elections are prepared. We are working with our federal partners to make sure those officials on the front lines of our elections have the information and the tools they need to combat Russian interference.”
“In 2020, we’re doing this and more to prevent our adversaries from degrading faith in our democracy and election results”, Wolf said.The acting secretary acknowledged that “100 percent security is never realistic” and asserted that US federal government and intelligence agencies were “laser-focused” on securing the upcoming elections.
Russian Trail
US intelligence agencies and lawmakers have accused Moscow of meddling in US elections since Trump’s 2016 victory, a political event that provoked allegations of Trump’s cooperation with Moscow as a means spreading anti-opponent propaganda online.
The US Department of Justice at the time launched an investigation headed by US Special Prosecutor Robert Mueller but the report concluded that no sufficient evidence existed to prove the allegations.
Both Trump and Russian officials have together repeatedly denied claims that they worked together to influence the results of the election.
In December 2019, Russian Foreign Minister Sergey Lavrov said that he had not seen any proof in support of allegations that Russia interfered in US elections, arguing that “No one has given us this proof because simply it does not exist”, while noting that Moscow is prepared to exchange assurances with Washington on non-interference in each other’s domestic affairs.Besides the US, the narrative of Russian involvement in the internal affairs of other countries has been used by a variety of European nations, however, again, no proof has been furnished.
In November 2019, El Pais published several stories alleging Russian influence in Catalonia, according to Spanish intelligence officers, again without providing evidence. The Russian embassy in Spain responded by joking about the allegations.
“With regards to the tireless work of El Pais researchers on linking the source of the Catalan crisis to Russia, we would like to draw their attention to a revealing fact. There is a suspicious coincidence: the number of the alleged Russian unit, which is mentioned in the newspaper, ends with 155, which itself creates a new reality. So – [follow] the trail,” the embassy tweeted.Spain’s constitution contains Article 155, used by Madrid to suspend Catalonia’s autonomy and violently introduce direct rule in the wake of a 2017 independence declaration.
How an Israeli Spy-Linked Tech Firm Gained Access to the US Gov’t’s Most Classified Networks

Graphic by Claudio Cabrera
By Whitney Webb | MintPress News | January 14, 2020
If the networks of the U.S. military, the U.S. intelligence community and a slew of other U.S. federal agencies were running the software of a company with deep ties, not only to foreign companies with a history of espionage against the U.S. but also foreign military intelligence, it would — at the very least — garner substantial media attention. Yet, no media reports to date have noted that such a scenario exists on a massive scale and that the company making such software recently simulated the cancellation of the 2020 election and the declaration of martial law in the United States.
Earlier this month, MintPress News reported on the simulations for the U.S. 2020 election organized by the company Cybereason, a firm led by former members of Israel’s military intelligence Unit 8200 and advised by former top and current officials in both Israeli military intelligence and the CIA. Those simulations, attended by federal officials from the FBI, DHS and the U.S. Secret Service, ended in disaster, with the elections ultimately canceled and martial law declared due to the chaos created by a group of hackers led by Cybereason employees.
The first installment of this three part series delved deeply into Cybereason’s ties to the intelligence community of Israel and also other agencies, including the CIA, as well as the fact that Cybereason stood to gain little financially from the simulations given that their software could not have prevented the attacks waged against the U.S.’ electoral infrastructure in the exercise.
Also noted was the fact that Cybereason software could be potentially used as a backdoor by unauthorized actors, a possibility strengthened by the fact that the company’s co-founders all previously worked for firms that have a history of placing backdoors into U.S. telecommunications and electronic infrastructure as well as aggressive espionage targeting U.S. federal agencies.
The latter issue is crucial in the context of this installment of this exclusive MintPress series, as Cybereason’s main investors turned partners have integrated Cybereason’s software into their product offerings. This means that the clients of these Cybereason partner companies, the U.S. intelligence community and military among them, are now part of Cybereason’s network of more than 6 million endpoints that this private company constantly monitors using a combination of staff comprised largely of former intelligence operatives and an AI algorithm first developed by Israeli military intelligence.
Cybereason, thus far, has disclosed the following groups as lead investors in the company: Charles River Ventures (CRV), Spark Capital, Lockheed Martin and SoftBank. Charles River Ventures (CRV) was among the first to invest in Cybereason and has been frequently investing in other Israeli tech start-ups that were founded by former members of the elite Israeli military intelligence Unit 8200 over the last few years. Spark Capital, based in California, appears to have followed CRV’s interest in Cybereason since the venture capitalist who co-founded Spark and led its investment in Cybereason is a former CRV partner who still has close ties to the firm.
While CRV and Spark Capital seem like just the type of investors a company like Cybereason would attract given their clear interest in similar tech start-ups coming out of Israel’s cyber sector, Cybereason’s other lead investors — Lockheed Martin and SoftBank — deserve much more attention and scrutiny.
Cybereason widely used by US Government, thanks to Lockheed
“A match made in heaven,” trumpeted Forbes at the news of the Lockheed Martin-Cybereason partnership, first forged in 2015. The partnership involved not only Lockheed Martin becoming a major investor in the cybersecurity company but also in Lockheed Martin becoming the largest conduit providing Cybereason’s software to U.S. federal and military agencies.
Indeed, as Forbes noted at the time, not only did Lockheed invest in the company, it decided to integrate Cybereason’s software completely into its product portfolio, resulting in a “model of both using Cybereason internally, and selling it to both public and private customers.”
Cybereason CEO and former offensive hacker for Israeli military intelligence — Lior Div — said the following of the partnership:
Lockheed Martin invested in Cybereason’s protection system after they compared our solution against a dozen others from the top industry players. The US firm was so impressed with the results they got from Cybereason that they began offering it to their own customers – among them most of the top Fortune 100 companies, and the US federal government. Cybereason is now the security system recommended by LM to its customers for protection from a wide (sic) malware and hack attacks.”
Rich Mahler, then-director of Commercial Cyber Services at Lockheed Martin, told Defense Daily that the company’s decision to invest in Cybereason, internally use its software, and include the technology as part of Lockheed Martin’s cyber solutions portfolio were all “independent business decisions but were all coordinated and timed with the transaction.”
How independent each of those decisions actually was is unclear, especially given the timing of Lockheed Martin’s investment in Cybereason, whose close and troubling ties to Israeli intelligence as well as the CIA were noted in the previous installment of this investigative series. Indeed, about a year prior to their investment in the Israeli military intelligence-linked Cybereason, Lockheed Martin opened an office in Beersheba, Israel, where the IDF has its “cyberhub”. The office is focused not on the sales of armaments, but instead on technology.
Marilyn Hewson, Lockheed Martin’s CEO, said the following during her speech that inaugurated the company’s Beersheba office:
The consolidation of IDF Technical Units to new bases in the Negev Desert region is an important transformation of Israel’s information technology capability… We understand the challenges of this move. Which is why we are investing in the facilities and people that will ensure we are prepared to support for these critical projects. By locating our new office in the capital of the Negev we are well positioned to work closely with our Israeli partners and stand ready to: accelerate project execution, reduce program risk and share our technical expertise by training and developing in-country talent.”
Beersheba not only houses the IDF’s technology campus, but also the Israel National Cyber Directorate, which reports directly to Israel’s Prime Minister, as well as a high-tech corporate park that mostly houses tech companies with ties to Israel’s military intelligence apparatus. The area has been cited in several media reports as a visible indicator of the public-private merger between Israeli technology companies, many of them started by Unit 8200 alumni, and the Israeli government and its intelligence services. Lockheed Martin quickly became a key fixture in the Beersheba-based cyberhub.
Not long before Lockheed began exploring the possibility of opening an office in Beersheba, the company was hacked by individuals who used tokens tied to the company, RSA Security, whose founders have ties to Israel’s defense establishment and which is now owned by Dell, a company also deeply tied to the Israeli government and tech sector. The hack, perpetrated by still unknown actors, may have sparked Lockheed’s subsequent interest in Israel’s cybersecurity sector.
Soon after opening its Beersheba office, Lockheed Martin created its Israel subsidiary, Lockheed Martin Israel. Unlike many of the company’s other subsidiaries, this one is focused exclusively on “cybersecurity, enterprise information technology, data centers, mobile, analytics and cloud” as opposed to the manufacture and design of armaments.

Marillyn Hewson, center, poses with Israeli gov. officials at the opening of Lockheed Martin’s facility in Beersheba. Photo | Diego Mittleberg
Haden Land, then-vice president of research and technology for Lockheed Martin, told the Wall Street Journal that the creation of the subsidiary was largely aimed at securing contracts with the IDF and that the company’s Israel subsidiary would soon be seeking partnership and investments in pursuit of that end. Land oversaw the local roll-out of the company’s Israel subsidiary while concurrently meeting with Israeli government officials. According to the Journal, Land “oversees all of Lockheed Martin’s information-systems businesses, including defense and civilian commercial units” for the United States and elsewhere.
Just a few months later, Lockheed Martin partnered and invested in Cybereason, suggesting that Lockheed’s decision to do so was aimed at securing closer ties with the IDF. This further suggests that Cybereason still maintains close ties to Israeli military intelligence, a point expounded upon in great detail in the previous installment of this series.
Thus, it appears that not only does Lockheed Martin use Cybereason’s software on its own devices and on those it manages for its private and public sector clients, but it also decided to use the company’s software in this way out of a desire to more closely collaborate with the Israeli military in matters related to technology and cybersecurity.
The cozy ties between Lockheed Martin, one of the U.S. government’s largest private contractors, and the IDF set off alarm bells, then and now, for those concerned with U.S. national security. Such concern makes it important to look at the extent of Cybereason’s use by federal and military agencies in the United States through their contracting of Lockheed Martin’s Information Technology (IT) division. This is especially important considering Israeli military intelligence’s history of using espionage, blackmail and private tech companies against the U.S. government, as detailed here.
While the exact number of U.S. federal and military agencies using Cybereason’s software is unknown, it is widespread, with Lockheed Martin’s IT division as the conduit. Indeed, Lockheed Martin was the number one IT solutions provider to the U.S. federal government up until its IT division was spun off and merged with Leidos Holdings. As a consequence, Leidos is now the largest IT provider to the U.S. government and is also directly partnered with Cybereason in the same way Lockheed Martin was. Even after its IT division was spun off, Lockheed Martin continues to use Cybereason’s software in its cybersecurity work for the Pentagon and still maintains a stake in the company.
The Leidos-Lockheed Martin IT hybrid provides a litany of services to the U.S. military and U.S. intelligence. As investigative journalist Tim Shorrock noted for The Nation, the company does “everything from analyzing signals for the NSA to tracking down suspected enemy fighters for US Special Forces in the Middle East and Africa” and, following its merger with Lockheed and consequential partnership with Cybereason, became “the largest of five corporations that together employ nearly 80 percent of the private-sector employees contracted to work for US spy and surveillance agencies.” Shorrock also notes that these private-sector contractors now dominate the mammoth U.S. surveillance apparatus, many of them working for Leidos and — by extension — using Cybereason’s software.
Leidos’ exclusive use of Cybereason software for cybersecurity is also relevant for the U.S. military since Leidos runs a number of sensitive systems for the Pentagon, including its recently inked contract to manage the entire military telecommunications infrastructure for Defense Information Systems Agency (DISA). In addition to maintaining the military telecom network, Cybereason is also directly partnered with World Wide Technologies (WWT) as of this past October. WWT manages cybersecurity for the U.S. Army, maintains DISA’s firewalls and data storage as well as the U.S. Air Force’s biometric identification system. WWT also manages contracts for NASA, itself a frequent target of Israeli government espionage, and the U.S. Navy. WWT’s partnership is similar to the Lockheed/Leidos partnership in that Cybereason’s software is now completely integrated into its portfolio, giving the company full access to the devices on all of these highly classified networks.
Many of these new partnerships with Cybereason, including its partnership with WWT, followed claims made by members of Israel’s Unit 8200 in 2017 that the popular antivirus software of Kaspersky Labs contained a backdoor for Russian intelligence, thereby compromising U.S. systems. The Wall Street Journal was the first to report on the alleged backdoor but did not mention the involvement of Unit 8200 in identifying it, a fact revealed by the New York Times a week later.
Notably, none of the evidence Unit 8200 used to blame Kaspersky has been made public and Kaspersky noted that it was actually Israeli hackers that had been discovered planting backdoors into its platform prior to the accusation levied against Kaspersky by Unit 8200. As the New York Times noted:
Investigators later discovered that the Israeli hackers had implanted multiple back doors into Kaspersky’s systems, employing sophisticated tools to steal passwords, take screenshots, and vacuum up emails and documents.”
Unit 8200’s claims ultimately led the U.S. government to abandon Kaspersky’s products entirely in 2018, allowing companies like Cybereason (with its own close ties to Unit 8200) to fill the void. Indeed, the very agencies that banned Kaspersky now use cybersecurity software that employs Cybereason’s EDR system. No flags have been raised about Cybereason’s own collaboration with the very foreign intelligence service that first pointed the finger at Kaspersky and that previously sold software with backdoors to sensitive U.S. facilities.
SoftBank, Cybereason and the Vision Fund
While its entry into the U.S. market and U.S. government networks is substantial, Cybereason’s software is also run throughout the world on a massive scale through partnerships that have seen it enter into Latin American and European markets in major ways in just the last few months. It has also seen its software become prominent in Asia following a partnership with the company Trustwave. Much of this rapid expansion followed a major injection of cash courtesy of one of the company’s biggest clients and now its largest investor, Japan’s SoftBank.
SoftBank first invested in Cybereason in 2015, the same year Lockheed Martin initially invested and partnered with the firm. It was also the year that SoftBank announced its intention to invest in Israeli tech start-ups. SoftBank first injected $50 million into Cybereason, followed by an additional $100 million in 2017 and $200 million last August. SoftBank’s investments account for most of the money raised by the company since it was founded in 2012 ($350 million out of $400 million total).

Cybereason CEO Lior Div speaks at a SoftBank event in Japan, July 21, 2017. Photo | Cybereason
Prior to investing, Softbank was a client of Cybereason, which Ken Miyauchi, president of SoftBank, noted when making the following statement after Softbank’s initial investment in Cybereason:
SoftBank works to obtain cutting edge technology and outstanding business models to lead the Information Revolution. Our deployment of the Cybereason platform internally gave us firsthand knowledge of the value it provides, and led to our decision to invest. I’m confident Cybereason and SoftBank’s new product offering will bring a new level of security to Japanese organizations.”
SoftBank — one of Japan’s largest telecommunications companies — not only began to deploy Cybereason internally but directly partnered with it after investing, much like Lockheed Martin had done around the same time. This partnership resulted in SoftBank and Cybereason creating a joint venture in Japan and Cybereason creating partnerships with other tech companies acquired by SoftBank, including the U.K.’s Arm, which specializes in making chips and management platforms for Internet of Things (IoT) devices.
SoftBank’s interest in Cybereason is significant, particularly in light of Cybereason’s interest in the 2020 U.S. election, given that SoftBank has significant ties to key allies of President Trump and even the president himself.
Indeed, SoftBank’s Masayoshi Son was among the first wave of international business leaders who sought to woo then-president-elect Trump soon after the 2016 election. Son first visited Trump Tower in December 2016 and announced, with Trump by his side in the building’s lobby, that SoftBank would invest $50 billion in the U.S. and create 50,000 jobs. Trump subsequently claimed on Twitter that Son had only decided to make this investment because Trump had won the election.
Son told reporters at the time that the investment would come from a $100 billion fund that would be created in partnership with Saudi Arabia’s sovereign wealth fund as well as other investors. “I just came to celebrate his new job. I said, ‘This is great. The US will become great again,’” Son said, according to reports.
Then, in March of 2017, Son sent top SoftBank executives to meet with senior members of Trump’s economic team and, according to the New York Times, “the SoftBank executives said that because of a lack of advanced digital investments, the competitiveness of the United States economy was at risk. And the executives made the case, quite strongly, that Mr. Son was committed to playing a major role in addressing this issue through a spate of job-creating investments.” Many of SoftBank’s investments and acquisitions in the U.S. since then have focused mainly on artificial intelligence and technology with military applications, such as “killer robot” firm Boston Dynamics, suggesting Son’s interest lies more in dominating futuristic military-industrial technologies than creating jobs for the average American.
After their initial meeting, Trump and Son met again a year later in June 2018, with Trump stating that “His [Son’s] $50 billion turned out to be $72 billion so far, he’s not finished yet.” Several media reports have claimed that Son’s moves since Trump’s election have sought to “curry favor” with the President.
Through the creation of this fund alongside the Saudis, SoftBank has since become increasingly intertwined with Saudi Crown Prince Muhammad bin Salman (MBS), a key ally of President Trump in the Middle East known for his authoritarian crackdowns on Saudi elites and dissidents alike. The ties between Saudi Arabia and SoftBank became ever tighter when MBS took the reins in the oil kingdom and after SoftBank announced the launch of the Vision Fund in 2016. SoftBank’s Vision Fund is a vehicle for investing in hi-tech companies and start-ups and its largest shareholder is the Public Investment Fund of Saudi Arabia. Notably, Son decided to launch the Vision Fund in Riyadh during President Trump’s first official visit to the Gulf Kingdom.

Masayoshi Son, left, signs a deal related to the Vision Fund with Bin Salman in March 2018. Photo | SPA
In addition, the Mubadala Investment Company, a government fund of the United Arab Emirates (UAE), gave $15 billion to the Vision Fund. UAE leadership also share close ties to the Trump administration and MBS in Saudi Arabia.
As a consequence, SoftBank’s Vision Fund is majority funded by two Middle Eastern authoritarian governments with close ties to the U.S. government, specifically the Trump administration. In addition, both countries have enjoyed the rapid growth and normalization of ties with the state of Israel in recent years, particularly following the rise of current Saudi Crown Prince Muhammad bin Salman and Jared Kushner’s rise to prominence in his father-in-law’s administration. Other investments in the Vision Fund have come from Apple, Qualcomm and Oracle’s Larry Ellison, all tech companies with strong ties to Israel’s government.
The Saudi and Emirati governments’ links to the Vision Fund are so obvious that even mainstream outlets like the New York Times have described them as a “front for Saudi Arabia and perhaps other countries in the Middle East.”
SoftBank also enjoys close ties to Jared Kushner, with Fortress Investment Group lending $57 million to Kushner Companies in October 2017 while it was under contract to be acquired by SoftBank. As Barron’s noted at the time:
When SoftBank Group bought Fortress Investment Group last year, the Japanese company was buying access to a corps of seasoned investors. What SoftBank also got is a financial tie to the family of President Donald Trump’s senior advisor and son-in-law, Jared Kushner.”
According to The Real Deal, Kushner Companies obtained the financing from Fortress only after its attempts to obtain funding through the EB-5 visa program for a specific real estate venture were abandoned after the U.S. Attorney and the Securities and Exchange Commission began to investigate how Kushner Companies used the EB-5 investor visa program. A key factor in the opening of that investigation was Kushner Companies’ representatives touting Jared Kushner’s position at the White House when talking to prospective investors and lenders.
SoftBank also recently came to the aid of a friend of Jared Kushner, former CEO of WeWork Adam Neumann. Neumann made shocking claims about his ties to both Kushner and Saudi Arabia’s MBS, even asserting that he had worked with both in creating Kushner’s long-awaited and controversial Middle East “peace plan” and claimed that he, Kushner and MBS would together “save the world.” Neumann previously called Kushner his “mentor.” MBS has also discussed on several occasions his close ties with Kushner and U.S. media reports have noted the frequent correspondence between the two “princelings.”
Notably, SoftBank invested in Neumann’s WeWork using money from the Saudi-dominated Vision Fund and later went on to essentially bail the company out after its IPO collapse and Neumann was pushed out. SoftBank’s founder, Masayoshi Son, had an odd yet very close relationship with Neumann, perhaps explaining why Neumann was allowed to walk with $1.7 billion after bringing WeWork to the brink of collapse. Notably, nearly half of SoftBank’s approximately $47 billion investments in the U.S. economy since Trump’s election, went to acquiring and then bailing out WeWork. It is unlikely that such a disastrous investment resulted in the level of job creation that Son had promised Trump in 2016.
Given that it is Cybereason’s top investor and shareholder by a large margin, SoftBank’s ties to the Trump administration and key allies of that administration are significant in light of Cybereason’s odd interest in 2020 U.S. election scenarios that end with the cancellation of this year’s upcoming presidential election. It goes without saying that the cancellation of the election would mean a continuation of the Trump administration until new elections would take place.
Furthermore, with Cybereason’s close and enduring ties to Israeli military intelligence now well-documented, it is worth asking if Israeli military intelligence would consider intervening in 2020 if the still-to-be-decided Democratic contender was strongly opposed to Israeli government policy, particularly Israel’s military occupation of Palestine. This is especially worth considering given revelations that sexual blackmailer and pedophile Jeffrey Epstein, who targeted prominent U.S. politicians, mostly Democrats, was in the employ of Israeli military intelligence.
Notably, Cybereason’s doomsday election scenarios involved the weaponization of deep fakes, self-driving cars and the hacking Internet of Things devices, with all of those technologies being pioneered and perfected — not by Russia, China or Iran — but by companies directly tied to Israeli intelligence, much like Cybereason itself. These companies, their technology and Cybereason’s own work creating the narrative that U.S. rival states seek to undermine the U.S. election in this way, will all be discussed in the conclusion of MintPress’ series on Cybereason and its outsized interest in the U.S. democratic process.
Whitney Webb is a MintPress News journalist based in Chile. She has contributed to several independent media outlets including Global Research, EcoWatch, the Ron Paul Institute and 21st Century Wire, among others. She has made several radio and television appearances and is the 2019 winner of the Serena Shim Award for Uncompromised Integrity in Journalism.
Now It’s Official: US Visa Can Be Denied If You (Or Even Your Friends) Are Critical of American Policies
By Philip Giraldi | Strategic Culture Foundation | September 5, 2019
There have been several interesting developments in the United States government’s war on free speech and privacy. First of all, the Department of Homeland Security’s (DHS) Customs and Border Protection Agency (CBP), which is responsible for actual entry of travelers into the country, has now declared that it can legally access phones and computers at ports of entry to determine if there is any subversive content which might impact on national security. “Subversive content” is, of course, subjective, but those seeking entry can be turned back based on how a border control agent perceives what he is perusing on electronic media.
Unfortunately, the intrusive nature of the procedure is completely legal, particularly as it applies to foreign visitors, and is not likely to be overturned in court in spite of the Fourth Amendment’s constitutional guarantee that individuals should “… be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures.” Someone at a port of entry is not legally inside the United States until he or she has been officially admitted. And if that someone is a foreigner, he or she has no right by virtue of citizenship even to enter the country until entry has been permitted by an authorized US Customs and Border Protection official. And that official can demand to see anything that might contribute to the decision whether or not to let the person enter.
And there’s more to it than just that. Following the Israeli model for blocking entry of anyone who can even be broadly construed as supporting a boycott, the United States now also believes it should deny admittance to anyone who is critical of US government policy, which is a reversal of previous policy that considered political opinions to be off-limits for visa denial. DHS, acting in response to pressure from the White House, now believes it can adequately determine hostile intent from the totality of what appears on one’s phone or laptop, even if the material in question was clearly not put on the device by the owner. In other words, if a traveler has an email sent to him or her by someone else that complains about behavior by the United States government, he or she is responsible for that content.
One interesting aspect of the new policy is that it undercuts the traditional authority of US Embassies and Consulates overseas to issue visas to foreigners. The State Department visa process is rigorous and can include employment and real property verification, criminal record checks, social media reviews and Google-type searches. If there is any doubt about the visa applicant, entry into the US is denied. With the new DHS measures in place, this thoroughly vetted system is now sometimes being overruled by a subjective judgment made by someone who is not necessarily familiar with the traveler’s country or even regarding the threat level that being a citizen of that country actually represents.
Given the new rules regarding entering the United States, it comes as no surprise that the story of an incoming Harvard freshman who was denied entry into the United States after his laptop and cellphone were searched at Boston’s Logan Airport has been making headlines. Ismail Ajjawi, a 17-year-old Palestinian resident of Lebanon, was due to begin classes as a freshman, but he had his student visa issued in by the US Embassy in Beirut rejected before being flown back to Lebanon several hours later.
Ajjawi was questioned by one immigration officer who asked him repeatedly about his religion before requiring him to turn over his laptop and cell phone. Some hours later, the questioning continued about Ajjawi’s friends and associates, particularly those on social media. At no point was Ajjawi accused of having himself written anything that was critical of the United States and the interrogation rather centered on the views expressed by his friends.
The decision to ban Ajjawi produced such an uproar worldwide that it was reversed a week later, apparently as a result of extreme pressure exerted by Harvard University. Nevertheless, the decisions to deny entry are often arbitrary or even based on bad information, but the traveler normally has no practical recourse to reverse the process. And the number of such searches is going up dramatically, numbering more than 30,000 in 2017, some of which have been directed against US residents. Even though permanent resident green card holders and citizens have a legal right to enter the United States, there are reports that they too are having their electronic media searched. That activity is the subject of an American Civil Liberties Union (ACLU) lawsuit against the Department of Homeland Security that is currently working its way through the courts. The ACLU is representing 10 American citizens and a legal permanent resident who had their media searched without a warrant as required by the Fourth Amendment.
It is believed that many of the arbitrary “enforcements” by the CBP are carried out by the little-known Tactical Response Team (TRT) that targets certain travelers that fit a profile. DHS officials confirmed in September 2017 that 1,400 visa holders had been denied entry due to TRT follow-up inspections. And there are also reports of harassment of American citizens by possible TRT officials. A friend of mine was returning from Portugal to a New York Area airport when he was literally pulled from the queue as he was departing the plane. A Customs agent at the jetway was repeatedly calling out his birth date and then also added his name. He was removed from the line and taken to an interrogation room where he was asked to identify himself and then queried regarding his pilot’s license. He was then allowed to proceed with no other questions, suggesting that it was all harassment of a citizen base on profiling pure and simple.
My friend is a native-born American who has a Master’s degree and an MBA, is an army veteran and has no criminal record, not even a parking ticket. He worked for an American bank in the Middle East more than thirty years ago, which, together with the pilot’s license, might be the issue these days with a completely paranoid federal government constantly on the lookout for more prey “to keep us safe.” Unfortunately, keeping us safe has also meant that freedom of speech and association as well as respect for individual privacy have all been sacrificed. As America’s Founding Father Benjamin Franklin once reportedly observed, “Those who would give up essential Liberty to purchase a little temporary Safety will wind up with neither.”
Big Tech & Big Brother meet at Facebook HQ to discuss how to ‘secure’ US elections
RT | September 5, 2019
Security teams for Facebook, Google, Twitter and Microsoft met with the FBI, the Department of Homeland Security and the Director of National Intelligence’s office to coordinate a strategy to win – er, secure – the 2020 elections.
The tech platforms met with government officials at Facebook’s Menlo Park headquarters on Wednesday, the company has confirmed, boasting that Big Tech and Big Brother have developed a “comprehensive strategy” to get control of previous election-related “vulnerabilities” while “analyzing and getting ahead of new threats.”
Facebook has scrambled to get in front of the 2020 election after being blamed for Trump’s 2016 electoral victory over merely allowing the “Russian trolls” to buy a bunch of ads, most of which appeared after the vote and had nothing to do with the election. But the company insisted last week it had tightened its rules for verifying purchasers of “political” ads, for real this time, after the 2018 contest showed they could still be duped into running obviously-fake ads “paid for by” the Islamic State terror group and Cambridge Analytica.
Aside from the occasional purge of accounts accused of being linked to countries like Russia, Iran, and China on the US’ ever-lengthening enemies’ list, however, it’s hard to tell what exactly any platform has done to make itself immune to ‘manipulation’. Twitter banned state-owned media from buying ads on its platform last month, holding the move up as a victory against the dreaded “foreign meddling,” but its own founder’s account was hacked last week, suggesting it has bigger security issues than a few wrongthink-prone advertisers.
And Google’s potential to sway elections has been the subject of Senate hearings – yet the company has remained silent on addressing the problem, suggesting it doesn’t see it as a bug at all, but a feature. Subsidiary YouTube, meanwhile, conducted another round of deplatforming last month even while declaring it was an open platform for controversial ideas.
The electoral meeting of the minds came less than a week after the Pentagon’s Defense Advanced Projects Research Agency (DARPA) declared war on deepfakes and other potentially discord-sowing information, promising to neutralize all “malicious” content within four years – if not for this election, then certainly for the next.
Until then, there’s Microsoft’s ElectionGuard software, which the company announced in July it would provide to all the nation’s voting machines, free of charge, out of the goodness of its (and the Pentagon-owned contractor that helped develop the program’s) heart. And if Microsoft’s act of selfless charity doesn’t convince a district their democracy is worth protecting, there’s always Cyberdome, the election security nonprofit advised by half a dozen former intel agency heads who want what’s best for your vote (when they’re not authorizing torture or warrantless wiretapping).
Getting the DHS involved was a nice touch, too, after that agency was accused of attempting to hack electoral systems in multiple states thousands of times during the period surrounding the 2016 election. Unlike the “Russian hacking” allegations that remain unproven, multiple officials from Idaho, Georgia, Indiana, West Virginia, and Kentucky claim the agency attempted to access their systems after they opposed its efforts to “secure” those systems. After initially denying any involvement, the DHS claimed the attempted breach alarms were set off accidentally, during routine “legitimate work.”
Law Enforcement To Flag & Spy On Future Criminals
DHS’s (old) Risk Assessment Chart
MassPrivateI | August 20, 2019
America’s fear of mass-shootings is about to take a truly bizarre turn. That’s because our law enforcement will soon be used as fortune tellers to spy on future criminals.
How will law enforcement be used as fortune tellers?
A recent Albuquerque Journal article revealed that law enforcement will flag people that they think might pose a potential risk.
“Gov. Michelle Lujan Grisham directed state Homeland Security and Emergency Management Secretary Jackie Lindsay to start enrolling all 33 county sheriffs in a data-sharing program so that individuals deemed a potential risk could be flagged and monitored.”
What types of things could Americans do that law enforcement would consider threatening?
Inside Sources revealed that police would be looking for “certain indicators.”
State Police Chief Tim Johnson said, “I think it’s obviously important for all of the citizens of New Mexico to be on the lookout for certain indicators of these types of folks that would do this. And part of our job as government officials is to ensure that the citizens of the community understand what those indicators are so they can report them.”
The Tampa Bay Times reports that police are looking for “certain critical threat indicators” on students social media posts and have even created their own FortifyFL app that allows anyone to secretly report suspicious behavior.
What these “indicators” are is anyone’s guess.
Johnson also said that it was “important for law enforcement and other social services to follow up” on reports of possibly dangerous citizens “in the hopes of preventing” acts of domestic terrorism.
Law enforcement and other agencies are being encouraged to report on and flag anyone that they deem a “potential risk.”
What could possibly go wrong?
It was only a couple of months ago, when I warned people about the “Threat Assessment, Prevention and Safety Act” that basically allows law enforcement to label anyone a potential threat.
“The TAPS Act would encourage law enforcement to give everyone a personal threat assessment (kids and adults) and single out those that they deem as future threats.”
Police across the country are already using “red flag” laws to take weapons away from people they deem a potential threat. So why is Homeland Security creating a whole new class of suspicious people?
Because the War on Terror constantly needs new enemies if it is to keep Americans living in fear.
The Albuquerque Journal revealed how law enforcement plans to use the red flag bill to allow law enforcement and other agencies to give people secret threat ratings.
“Sheriffs had been working with the Democratic sponsor of a proposed red flag bill toward a possible compromise. In its original form, the bill would have allowed courts to order the temporary taking of guns from someone deemed an immediate threat, “San Juan County Sheriff Shane Ferrari said.
From Homeland Security spying on everyone’s social media posts to the FBI, it seems like no one is safe from Big Brother’s prying eyes.
Reason.com warned that the FBI’s “red flag” social media spying tool is “a meme-illiterate Facebook-stalking precog from the Minority Report.”
Reason also warned that spying on everyone’s social media posts could spiral out of control.
“There are operations centers and watch floors, which monitor news and events to create reports for the relevant FBI team. These would spur the activation of fusion center, tactical teams which use early notification and accurate geo-locations. Which could allow law enforcement to target and even disenfranchise social media users whose posts may have been misinterpreted.”
Placing people on a secret risk chart is a disaster waiting to happen, just ask those people on the no-fly list or terror watch list.
There are no law enforcement risk rating charts yet.
Based on DHS’s old risk advisory chart we could expect law enforcement to use something similar to Canada’s workplace risk assessment ratings chart:

Canada’s workplace risk assessment ratings chart is a disturbing example of how DHS could give everyone a personal risk assessment.
Asking law enforcement to guess who might become a criminal is at best fortune telling; and at worst, an excuse to incarcerate more people.
How the Department of Homeland Security Created a Deceptive Tale of Russia Hacking US Voter Sites
By Gareth Porter | Consortium News | August 28, 2018
The narrative of Russian intelligence attacking state and local election boards and threatening the integrity of U.S. elections has achieved near-universal acceptance by media and political elites. And now it has been accepted by the Trump administration’s intelligence chief, Dan Coats, as well.
But the real story behind that narrative, recounted here for the first time, reveals that the Department of Homeland Security (DHS) created and nurtured an account that was grossly and deliberately deceptive.
DHS compiled an intelligence report suggesting hackers linked to the Russian government could have targeted voter-related websites in many states and then leaked a sensational story of Russian attacks on those sites without the qualifications that would have revealed a different story. When state election officials began asking questions, they discovered that the DHS claims were false and, in at least one case, laughable.
The National Security Agency and special counsel Robert Mueller’s investigating team have also claimed evidence that Russian military intelligence was behind election infrastructure hacking, but on closer examination, those claims turn out to be speculative and misleading as well. Mueller’s indictment of 12 GRU military intelligence officers does not cite any violations of U.S. election laws though it claims Russia interfered with the 2016 election.
A Sensational Story
On Sept. 29, 2016, a few weeks after the hacking of election-related websites in Illinois and Arizona, ABC News carried a sensational headline: “Russian Hackers Targeted Nearly Half of States’ Voter Registration Systems, Successfully Infiltrated 4.” The story itself reported that “more than 20 state election systems” had been hacked, and four states had been “breached” by hackers suspected of working for the Russian government. The story cited only sources “knowledgeable” about the matter, indicating that those who were pushing the story were eager to hide the institutional origins of the information.
Behind that sensational story was a federal agency seeking to establish its leadership within the national security state apparatus on cybersecurity, despite its limited resources for such responsibility. In late summer and fall 2016, the Department of Homeland Security was maneuvering politically to designate state and local voter registration databases and voting systems as “critical infrastructure.” Such a designation would make voter-related networks and websites under the protection a “priority sub-sector” in the DHS “National Infrastructure Protection Plan, which already included 16 such sub-sectors.
DHS Secretary Jeh Johnson and other senior DHS officials consulted with many state election officials in the hope of getting their approval for such a designation. Meanwhile, the DHS was finishing an intelligence report that would both highlight the Russian threat to U.S. election infrastructure and the role DHS could play in protecting it, thus creating political impetus to the designation. But several secretaries of state—the officials in charge of the election infrastructure in their state—strongly opposed the designation that Johnson wanted.
On Jan. 6, 2017—the same day three intelligence agencies released a joint “assessment” on Russian interference in the election—Johnson announced the designation anyway.
Media stories continued to reflect the official assumption that cyber attacks on state election websites were Russian-sponsored. Stunningly, The Wall Street Journal reported in December 2016 that DHS was itself behind hacking attempts of Georgia’s election database.
The facts surrounding the two actual breaches of state websites in Illinois and Arizona, as well as the broader context of cyberattacks on state websites, didn’t support that premise at all.
In July, Illinois discovered an intrusion into its voter registration website and the theft of personal information on as many as 200,000 registered voters. (The 2018 Mueller indictments of GRU officers would unaccountably put the figure at 500,000.) Significantly, however, the hackers only had copied the information and had left it unchanged in the database.
That was a crucial clue to the motive behind the hack. DHS Assistant Secretary for Cyber Security and Communications Andy Ozment told a Congressional committee in late September 2016 that the fact hackers hadn’t tampered with the voter data indicated that the aim of the theft was not to influence the electoral process. Instead, it was “possibly for the purpose of selling personal information.” Ozment was contradicting the line that already was being taken on the Illinois and Arizona hacks by the National Protection and Programs Directorate and other senior DHS officials.
In an interview with me last year, Ken Menzel, the legal adviser to the Illinois secretary of state, confirmed what Ozment had testified. “Hackers have been trying constantly to get into it since 2006,” Menzel said, adding that they had been probing every other official Illinois database with such personal data for vulnerabilities as well. “Every governmental database—driver’s licenses, health care, you name it—has people trying to get into it,” said Menzel.
In the other successful cyberattack on an electoral website, hackers had acquired the username and password for the voter database Arizona used during the summer, as Arizona Secretary of State Michele Reagan learned from the FBI. But the reason that it had become known, according to Reagan in an interview with Mother Jones, was that the login and password had shown up for sale on the dark web—the network of websites used by cyber criminals to sell stolen data and other illicit wares.
Furthermore, the FBI had told her that the effort to penetrate the database was the work of a “known hacker” whom the FBI had monitored “frequently” in the past. Thus, there were reasons to believe that both Illinois and Arizona hacking incidents were linked to criminal hackers seeking information they could sell for profit.
Meanwhile, the FBI was unable to come up with any theory about what Russia might have intended to do with voter registration data such as what was taken in the Illinois hack. When FBI Counterintelligence official Bill Priestap was asked in a June 2017 hearing how Moscow might use such data, his answer revealed that he had no clue: “They took the data to understand what it consisted of,” said the struggling Priestap, “so they can affect better understanding and plan accordingly in regards to possibly impacting future elections by knowing what is there and studying it.”
The inability to think of any plausible way for the Russian government to use such data explains why DHS and the intelligence community adopted the argument, as senior DHS officials Samuel Liles and Jeanette Manfra put it, that the hacks “could be intended or used to undermine public confidence in electoral processes and potentially the outcome.” But such a strategy could not have had any effect without a decision by DHS and the U.S. intelligence community to assert publicly that the intrusions and other scanning and probing were Russian operations, despite the absence of hard evidence. So DHS and other agencies were consciously sowing public doubts about U.S. elections that they were attributing to Russia.
DHS Reveals Its Self-Serving Methodology
In June 2017, Liles and Manfra testified to the Senate Intelligence Committee that an October 2016 DHS intelligence report had listed election systems in 21 states that were “potentially targeted by Russian government cyber actors.” They revealed that the sensational story leaked to the press in late September 2016 had been based on a draft of the DHS report. And more importantly, their use of the phrase “potentially targeted” showed that they were arguing only that the cyber incidents it listed were possible indications of a Russian attack on election infrastructure.
Furthermore, Liles and Manfra said the DHS report had “catalogued suspicious activity we observed on state government networks across the country,” which had been “largely based on suspected malicious tactics and infrastructure.” They were referring to a list of eight IP addresses an August 2016 FBI “flash alert” had obtained from the Illinois and Arizona intrusions, which DHS and FBI had not been able to attribute to the Russian government.

Manfra: No doubt it was the Russians. (C-SPAN)
The DHS officials recalled that the DHS began to “receive reports of cyber-enabled scanning and probing of election-related infrastructure in some states, some of which appeared to originate from servers operated by a Russian company.” Six of the eight IP addresses in the FBI alert were indeed traced to King Servers, owned by a young Russian living in Siberia. But as DHS cyber specialists knew well, the country of ownership of the server doesn’t prove anything about who was responsible for hacking: As cybersecurity expert Jeffrey Carr pointed out, the Russian hackers who coordinated the Russian attack on Georgian government websites in 2008 used a Texas-based company as the hosting provider.
The cybersecurity firm ThreatConnect noted in 2016 that one of the other two IP addresses had hosted a Russian criminal market for five months in 2015. But that was not a serious indicator, either. Private IP addresses are reassigned frequently by server companies, so there is not a necessary connection between users of the same IP address at different times.
The DHS methodology of selecting reports of cyber incidents involving election-related websites as “potentially targeted” by Russian government-sponsored hackers was based on no objective evidence whatever. The resulting list appears to have included any one of the eight addresses as well as any attack or “scan” on a public website that could be linked in any way to elections.
This methodology conveniently ignored the fact that criminal hackers were constantly trying to get access to every database in those same state, country and municipal systems. Not only for Illinois and Arizona officials, but state electoral officials.
In fact, 14 of the 21 states on the list experienced nothing more than the routine scanning that occurs every day, according to the Senate Intelligence Committee. Only six involved what was referred to as a “malicious access attempt,” meaning an effort to penetrate the site. One of them was in Ohio, where the attempt to find a weakness lasted less than a second and was considered by DHS’s internet security contractor a “non-event” at the time.
State Officials Force DHS to Tell the Truth
For a year, DHS did not inform the 21 states on its list that their election boards or other election-related sites had been attacked in a presumed Russian-sponsored operation. The excuse DHS officials cited was that it could not reveal such sensitive intelligence to state officials without security clearances. But the reluctance to reveal the details about each case was certainly related to the reasonable expectation that states would publicly challenge their claims, creating a potential serious embarrassment.
On Sept. 22, 2017, DHS notified 21 states about the cyber incidents that had been included in the October 2016 report. The public announcement of the notifications said DHS had notified each chief election officer of “any potential targeting we were aware of in their state leading up to the 2016 election.” The phrase “potential targeting” again telegraphed the broad and vague criterion DHS had adopted, but it was ignored in media stories.
But the notifications, which took the form of phone calls lasting only a few minutes, provided a minimum of information and failed to convey the significant qualification that DHS was only suggesting targeting as a possibility. “It was a couple of guys from DHS reading from a script,” recalled one state election official who asked not to be identified. “They said [our state] was targeted by Russian government cyber actors.”
A number of state election officials recognized that this information conflicted with what they knew. And if they complained, they got a more accurate picture from DHS. After Wisconsin Secretary of State Michael Haas demanded further clarification, he got an email response from a DHS official with a different account. “[B]ased on our external analysis,” the official wrote, “the WI [Wisconsin] IP address affected belongs to the WI Department of Workforce Development, not the Elections Commission.”
California Secretary of State Alex Padilla said DHS initially had notified his office “that Russian cyber actors ‘scanned’ California’s Internet-facing systems in 2016, including Secretary of State websites.” But under further questioning, DHS admitted to Padilla that what the hackers had targeted was the California Department of Technology’s network.
Texas Secretary of State Rolando Pablos and Oklahoma Election Board spokesman Byron Dean also denied that any state website with voter- or election-related information had been targeted, and Pablos demanded that DHS “correct its erroneous notification.”
Despite these embarrassing admissions, a statement issued by DHS spokesman Scott McConnell on Sept. 28, 2017 said the DHS “stood by” its assessment that 21 states “were the target of Russian government cyber actors seeking vulnerabilities and access to U.S. election infrastructure.” The statement retreated from the previous admission that the notifications involved “potential targeting,” but it also revealed for the first time that DHS had defined “targeting” very broadly indeed.
It said the category included “some cases” involving “direct scanning of targeted systems” but also cases in which “malicious actors scanned for vulnerabilities in networks that may be connected to those systems or have similar characteristics in order to gain information about how to later penetrate their target.”
It is true that hackers may scan one website in the hope of learning something that could be useful for penetrating another website, as cybersecurity expert Prof. Herbert S. Lin of Stanford University explained to me in an interview. But including any incident in which that motive was theoretical meant that any state website could be included on the DHS list, without any evidence it was related to a political motive.
Arizona’s further exchanges with DHS revealed just how far DHS had gone in exploiting that escape clause in order to add more states to its “targeted” list. Arizona Secretary of State Michele Reagan tweeted that DHS had informed her that “the Russian government targeted our voter registration systems in 2016.” After meeting with DHS officials in early October 2017, however, Reagan wrote in a blog post that DHS “could not confirm that any attempted Russian government hack occurred whatsoever to any election-related system in Arizona, much less the statewide voter registration database.”
What the DHS said in that meeting, as Reagan’s spokesman Matt Roberts recounted to me, is even more shocking. “When we pressed DHS on what exactly was actually targeted, they said it was the Phoenix public library’s computers system,” Roberts recalled.
In April 2018, a CBS News “60 Minutes” segment reported that the October 2016 DHS intelligence report had included the Russian government hacking of a “county database in Arizona.” Responding to that CBS report, an unidentified “senior Trump administration official” who was well-briefed on the DHS report told Reuters that “media reports” on the issue had sometimes “conflated criminal hacking with Russian government activity,” and that the cyberattack on the target in Arizona “was not perpetrated by the Russian government.”
NSA Finds a GRU Election Plot

National Security Agency headquarters in Fort Meade, Md. (Wikimedia)
NSA intelligence analysts claimed in a May 2017 analysis to have documented an effort by Russian military intelligence (GRU) to hack into U.S. electoral institutions. In an intelligence analysis obtained by The Intercept and reported in June 2017, NSA analysts wrote that the GRU had sent a spear-phishing email—one with an attachment designed to look exactly like one from a trusted institution but that contains malware design to get control of the computer—to a vendor of voting machine technology in Florida. The hackers then designed a fake web page that looked like that of the vendor. They sent it to a list of 122 email addresses NSA believed to be local government organizations that probably were “involved in the management of voter registration systems.” The objective of the new spear-phishing campaign, the NSA suggested, was to get control of their computers through malware to carry out the exfiltration of voter-related data.
But the authors of The Intercept story failed to notice crucial details in the NSA report that should have tipped them off that the attribution of the spear-phishing campaign to the GRU was based merely on the analysts’ own judgment—and that their judgment was faulty.
The Intercept article included a color-coded chart from the original NSA report that provides crucial information missing from the text of the NSA analysis itself as well as The Intercept’s account. The chart clearly distinguishes between the elements of the NSA’s account of the alleged Russian scheme that were based on “Confirmed Information” (shown in green) and those that were based on “Analyst Judgment” (shown in yellow). The connection between the “operator” of the spear-phishing campaign the report describes and an unidentified entity confirmed to be under the authority of the GRU is shown as a yellow line, meaning that it is based on “Analyst Judgment” and labeled “probably.”
A major criterion for any attribution of a hacking incident is whether there are strong similarities to previous hacks identified with a specific actor. But the chart concedes that “several characteristics” of the campaign depicted in the report distinguish it from “another major GRU spear-phishing program,” the identity of which has been redacted from the report.
The NSA chart refers to evidence that the same operator also had launched spear-phishing campaigns on other web-based mail applications, including the Russian company “Mail.ru.” Those targets suggest that the actors were more likely Russian criminal hackers rather than Russian military intelligence.
Even more damaging to its case, the NSA reports that the same operator who had sent the spear-phishing emails also had sent a test email to the “American Samoa Election Office.” Criminal hackers could have been interested in personal information from the database associated with that office. But the idea that Russian military intelligence was planning to hack the voter rolls in American Samoa, an unincorporated U.S. territory with 56,000 inhabitants who can’t even vote in U.S. presidential elections, is plainly risible.
The Mueller Indictment’s Sleight of Hand
The Mueller indictment of GRU officers released on July 13 appeared at first reading to offer new evidence of Russian government responsibility for the hacking of Illinois and other state voter-related websites. A close analysis of the relevant paragraphs, however, confirms the lack of any real intelligence supporting that claim.
Mueller accused two GRU officers of working with unidentified “co-conspirators” on those hacks. But the only alleged evidence linking the GRU to the operators in the hacking incidents is the claim that a GRU official named Anatoly Kovalev and “co-conspirators” deleted search history related to the preparation for the hack after the FBI issued its alert on the hacking identifying the IP address associated with it in August 2016.
A careful reading of the relevant paragraphs shows that the claim is spurious. The first sentence in Paragraph 71 says that both Kovalev and his “co-conspirators” researched domains used by U.S. state boards of elections and other entities “for website vulnerabilities.” The second says Kovalev and “co-conspirators” had searched for “state political party email addresses, including filtered queries for email addresses listed on state Republican Party websites.”

Mueller: Don’t read the fine print. (The White House/Wikimedia)
Searching for website vulnerabilities would be evidence of intent to hack them, of course, but searching Republican Party websites for email addresses is hardly evidence of any hacking plan. And Paragraph 74 states that Kovalev “deleted his search history”—not the search histories of any “co-conspirator”—thus revealing that there were no joint searches and suggesting that the subject Kovalev had searched was Republican Party emails. So any deletion by Kovalev of his search history after the FBI alert would not be evidence of his involvement in the hacking of the Illinois election board website.
With this rhetorical misdirection unraveled, it becomes clear that the repetition in every paragraph of the section of the phrase “Kovalev and his co-conspirators” was aimed at giving the reader the impression the accusation is based on hard intelligence about possible collusion that doesn’t exist.
The Need for Critical Scrutiny of DHS Cyberattack Claims
The DHS campaign to establish its role as the protector of U.S. electoral institutions is not the only case in which that agency has used a devious means to sow fear of Russian cyberattacks. In December 2016, DHS and the FBI published a long list of IP addresses as indicators of possible Russian cyberattacks. But most of the addresses on the list had no connection with Russian intelligence, as former U.S. government cyber-warfare officer Rob Lee found on close examination.
When someone at the Burlington, Vt., Electric Company spotted one of those IP addresses on one of its computers, the company reported it to DHS. But instead of quietly investigating the address to verify that it was indeed an indicator of Russian intrusion, DHS immediately informed The Washington Post. The result was a sensational story that Russian hackers had penetrated the U.S. power grid. In fact, the IP address in question was merely Yahoo’s email server, as Rob Lee told me, and the computer had not even been connected to the power grid. The threat to the power grid was a tall tale created by a DHS official, which the Post had to embarrassingly retract.
Since May 2017, DHS, in partnership with the FBI, has begun an even more ambitious campaign to focus public attention on what it says are Russian “targeting” and “intrusions” into “major, high value assets that operate components of our Nation’s critical infrastructure”, including energy, nuclear, water, aviation and critical manufacturing sectors. Any evidence of such an intrusion must be taken seriously by the U.S. government and reported by news media. But in light of the DHS record on alleged threats to election infrastructure and the Burlington power grid, and its well-known ambition to assume leadership over cyber protection, the public interest demands that the news media examine DHS claims about Russian cyber threats far more critically than they have up to now.
Gareth Porter is an independent investigative journalist and winner of the 2012 Gellhorn Prize for journalism. His latest book is Manufactured Crisis: The Untold Story of the Iran Nuclear Scare.
US Homeland Security wants to track journalists & analyze media ‘sentiment’
RT | April 7, 2018
The US Department of Homeland Security is looking to build a media monitoring database. When some reporters objected, a DHS spokesman dismissed their concerns as fodder for “black helicopter conspiracy theorists.”
Service providers who want to bid for the program have until April 13 to submit a capabilities statement, according to the notice posted on the federal contractor website by the National Protection and Programs Directorate (NPPD), a division of DHS charged with protecting the “physical and cyber infrastructure.”
This has led Michelle Fabio of Forbes to wonder if the DHS is trying to use the cries of “Russian meddling” to justify creating a database of journalists and social media influencers. When the Committee to Protect Journalists retweeted Fabio’s article, DHS spokesman Tyler Houlton chimed in to say the database is “nothing more than the standard practice of monitoring current events in the media.”
“Any suggestion otherwise is fit for tin foil hat wearing, black helicopter conspiracy theorists,” he added.
Houlton adopted a similar tone in responding to an inquiry from Alex Kasprak of the fact-checking site Snopes. “You are embarrassing yourself with these questions and wild conspiracy theories,” he wrote.
With Houlton being less than helpful, perhaps the Statement of Work attached to the bid request could shed some light on what the DHS is actually looking to build. According to the six-page document, the contractor shall “provide media comparison tools, design and rebranding tools, communication tools, and the ability to identify top media influencers.”
There are six tasks being required of the contractors, starting with the ability to track more than 290,000 global news sources in over 100 languages, “including Arabic, Chinese and Russian,” and the ability to instantly translate the articles to English.
The next step would be a password-protected online platform enabling the DHS to access search results on “online articles and social media conversations,” an interactive dashboard providing “real-time monitoring, analysis, and benchmark of media coverage” and the ability to analyze the coverage in terms of content, volume, sentiment, geographical spread, influencers, language and momentum, among other things.
All this should be available in an encrypted mobile app, with enabled email alerts and customer service support.
Most interestingly, listed under “Media engagement” is the ability to access “contact details and any other information that could be relevant,” for any influencer in the database, including the publications the influencer writes for, and an overview of the influencer’s previous coverage. This database would have to be searchable, including in languages such as Arabic, Chinese and Russian.
Oh, and any staff working on the contract would have to have appropriate security clearances, ranging from Secret all the way to Top Secret with SCI (Sensitive Compartmented Information).
The DHS spokesman’s snark has certainly raised some eyebrows, as official denials in Washington are never quite so forceful. One is reminded of how former Director of National Intelligence James Clapper told Congress the NSA does not “wittingly” spy on Americans. Unfortunately for Clapper, just a few months later whistleblower Edward Snowden showed the entire world that the NSA was doing just that.